Securing the Cloud with Defender for Cloud and Azure Policy
Learn how to drive security and compliance with Azure Policy and Defender For Cloud (Special Edition: Azure Skill Sprint January)
Introduction
The Cloud doesn’t have to feel overwhelming, and this January and February, we’re proving it. In collaboration with Jake Walsh, a Microsoft MVP, we’re kicking off the Azure Skill Sprint a community-focused initiative to empower others to grow their Azure expertise across different technology areas every Friday.
In this special edition blog, I’ll explore Azure Policy and Microsoft Defender for Cloud, two indispensable tools for establishing and maintaining a secure, compliant, and efficient cloud environment. Together, these tools help you enforce best practices, compliance, and proactively protect your workloads. Let’s explore their roles following a potential business scenario.
The Scenario: Securing the Enterprise Cloud
Imagine you’ve just joined an organisation as the Cloud Security Architect, tasked with ensuring the company’s cloud environment remains secure, compliant, and scalable. The business is expanding its digital footprint, leveraging Azure to power critical workloads. However, the leadership team has concerns about compliance risks, security gaps, and the complexity of managing resources at scale.
Your mission? To design and implement a robust governance and security framework that not only prevents misconfigurations but also ensures continuous compliance across every deployed resource all while keeping operations agile and efficient.
Setting the Stage: Identifying the Challenges
As you evaluate the environment, some key challenges become clear:
Misconfigurations: Resources are being deployed with inconsistent settings, such as missing encryption or exposed management ports, leading to vulnerabilities.
Compliance Concerns: Meeting regulatory standards like PCI DSS or ISO 27001 is difficult without centralised visibility into compliance status.
Scaling Governance: With multiple teams deploying resources, it’s challenging to enforce consistent standards without slowing innovation.
Fragmentation across the environment due to multiple tools, the security team gets lost in all the different portals and fragmented recommendations.
These issues echo industry-wide trends, with Gartner estimating that 99% of cloud security failures by 2025 will result from customer misconfigurations and inadequate practices. With the biggest danger remaining customers misconfiguring their cloud environments. The cloud isn’t inherently insecure, but managing it without clear policies and monitoring can open the door to vulnerabilities.
The Solution: Laying a Strong Foundation
To address these challenges, you decide to implement a two-pronged strategy:
Azure Policy: The blueprint for defining and enforcing standards. It ensures resources meet predefined compliance and security requirements from the moment they’re deployed.
Microsoft Defender for Cloud: The monitoring and security layer that provides continuous insights into your cloud environment’s posture, identifying risks and offering actionable remediation steps.
Azure policy
Building a strong foundation, this is where Azure Policy comes into play. Think of Azure Policy as your blueprint for cloud security and compliance. It helps you define and enforce rules that ensure every brick you lay every resource you deploy is secure and compliant according to your needs ( every environment is unique). Just like an architect uses precise measurements to ensure the walls are straight, Azure Policy enforces standards so your resources meet your organisation’s security and compliance requirements. Take the module below to find out in detail how azure policy works!
Azure policy initiatives
With a basic understanding of Azure Policy, you’ve laid the groundwork for creating a secure and compliant cloud environment. But as your organisation grows, so does the complexity of managing policies. You can’t afford to manage each policy individually it would be like trying to adjust every single bolt on a massive bridge by hand that’s where azure policy initiatives come in allowing you to group related policies into a single package tailored to a specific goal.
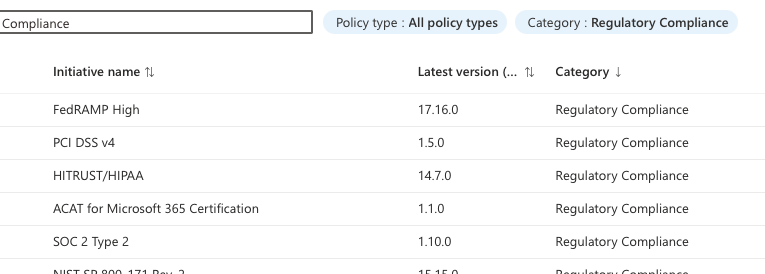
Azure policy Regulatory Compliance Standards
One of the leadership team’s biggest concerns was ensuring compliance with regulatory standards like PCI DSS or ISO 27001. Azure Policy addresses this challenge through its built-in Regulatory Compliance Standards. These standards come with predefined initiatives that group related policies to ensure your resources align with industry requirements. For example:
The PCI DSS Initiative enforces encryption, diagnostic logging, and secure networking for payment-related systems.
The ISO 27001 Initiative ensures consistent data protection and access control practices.
With Azure Policy, you can evaluate your environment against these standards in real time, identify non-compliant resources, and remediate issues quickly.
Azure policy enforcing best practices:
Another challenge raised by your organisation was the inconsistent deployment of resources, leading to non-uniform configurations and potential security risks. Azure Policy helps address this by enabling you to enforce best practice frameworks, such as the Microsoft Security Benchmark, which provides a comprehensive set of security controls aligned with industry standards.
Beyond industry frameworks, Azure Policy also allows you to create custom policies tailored to your organisation’s unique requirements. For example, you can enforce rules to:
Standardise resource configurations, such as requiring specific SKUs or regions.
Ensure all virtual machines are deployed with pre-configured network security groups (NSGs).
Mandate tagging for improved visibility and cost management.
By applying these policies, you can ensure resources are deployed consistently and securely, reducing risks while maintaining operational efficiency.
Azure policy enforcing governance at scale:
Your organisation is growing, with new teams spinning up resources daily. While this agility is great for innovation, it introduces complexity and the risk of inconsistent configurations. As the Cloud Security Architect, you need a governance solution that works not just for a single project but across all your subscriptions, resource groups, and environments.
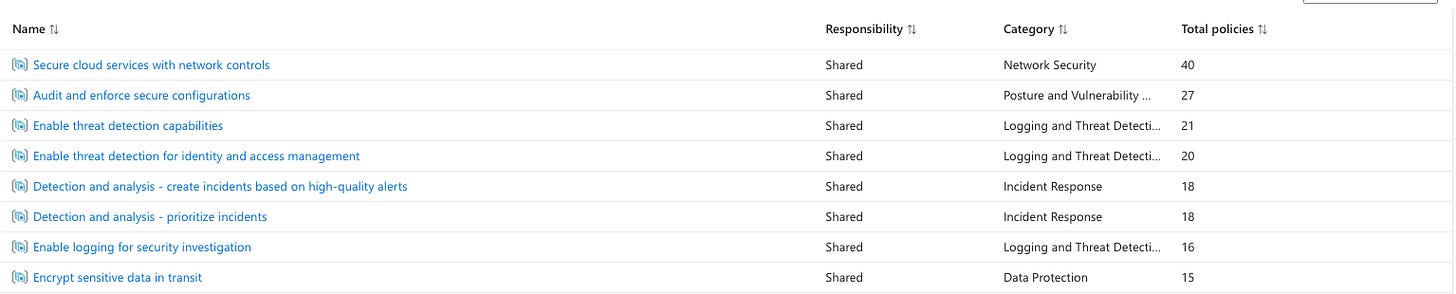
Azure Policy provides a scalable solution for enforcing governance across your environment. Policies can be applied at different scopes—management groups, subscriptions, or resource groups allowing you to align resource configurations with architectural frameworks like the Microsoft Azure Well-Architected Framework or Microsoft Cloud Adoption Framework.
These frameworks provide best practices for designing secure, scalable, and efficient cloud environments. Azure Policy ensures your deployments stay aligned by enforcing rules such as mandatory encryption, resource tagging, or network security group (NSG) requirements. For those using Infrastructure as Code (IaC) with tools like Bicep or Terraform, Azure Policy can validate compliance during deployments, creating a seamless integration between your design principles and operational processes.
Whether you’re deploying manually or programmatically, Azure Policy helps enforce the foundations of your architectural framework, ensuring every resource adheres to industry standards and organisational requirements. Take the modules below to find out how.
Combining Azure Policy and Architecture Frameworks:
Defender For Cloud
I hope you’re still with me! With Azure Policy in place, you’ve built a solid governance foundation, aligning your cloud environment with best practices and setting guardrails for secure deployments. But as we all know, governance alone isn’t enough. Your leadership team raised concerns about security gaps, fragmentation, and the need for ongoing monitoring to stay ahead of evolving threats. That’s where Microsoft Defender for Cloud a cloud native application protection platform ( CNAPP) steps in to help complete the picture. Luckily for you I have a five part series on the capabilities of CNAPPs and their inner workings start part one below.
How Defender for Cloud Complements Azure Policy
While Azure Policy ensures resources are deployed securely from the start, Defender for Cloud provides continuous monitoring and protection for your workloads, applications, data and infrastructure. It’s the layer of security that catches what happens after deployment and ensures your environment stays safe over time.
Here’s how it helps tackle key challenges:
Lack of Visibility: Modern cloud environments are complex, with resources scattered across virtual machines, containers, and serverless applications. Defender for Cloud gives you a centralised view of everything, so nothing goes unnoticed. Learn about cloud security posture below.
Misconfigurations and Compliance Gaps: Resources missing encryption, open ports, or other issues? Defender for Cloud doesn’t just identify these problems—it maps them to compliance standards like PCI DSS and ISO 27001, making it easy to take action and close the gaps.
Workload-Specific Threats: Defender for Cloud monitors for suspicious activity like unauthorised access attempts or brute-force attacks and provides actionable alerts to help you respond quickly.
How It All Comes Together
What makes Defender for Cloud so impactful is how seamlessly it integrates with Azure Policy. Together, they create a security loop that ensures your cloud is secure and compliant:
Azure Policy sets the rules: It enforces standards like encryption, resource tagging, and NSG requirements from day one.
Defender for Cloud keeps watch: It continuously monitors for misconfigurations, compliance gaps, and threats, providing actionable insights to keep your environment secure over time.
Wrapping Up: Your Next Steps
Thanks for joining me, and I hope you’ve learned something new! With Azure Policy setting the foundations and Defender for Cloud providing ongoing protection, you now have a comprehensive strategy to secure your cloud environment. These tools address the most common challenges of cloud-native security governance, visibility, and evolving threats all while keeping your environment aligned with best practices.
Where to Go from Here:
Take the applied skill challenge: show off your skills with the new Defender for Cloud Applied Skill
Check out the Azure Policy Community Tools:
Keep learning with the Defender For Cloud:
Check out Jakes LinkedIn and Blog for future skill sprint posts!
Have blog ideas, want to engage on a topic, or explore collaboration? Let’s take it offline reach out on LinkedIn. I’d love to connect and continue the conversation!