Part one: The value of a Cloud Native Application Protection Platform (CNAPP)
Why CNAPPs are essential for modern cloud security
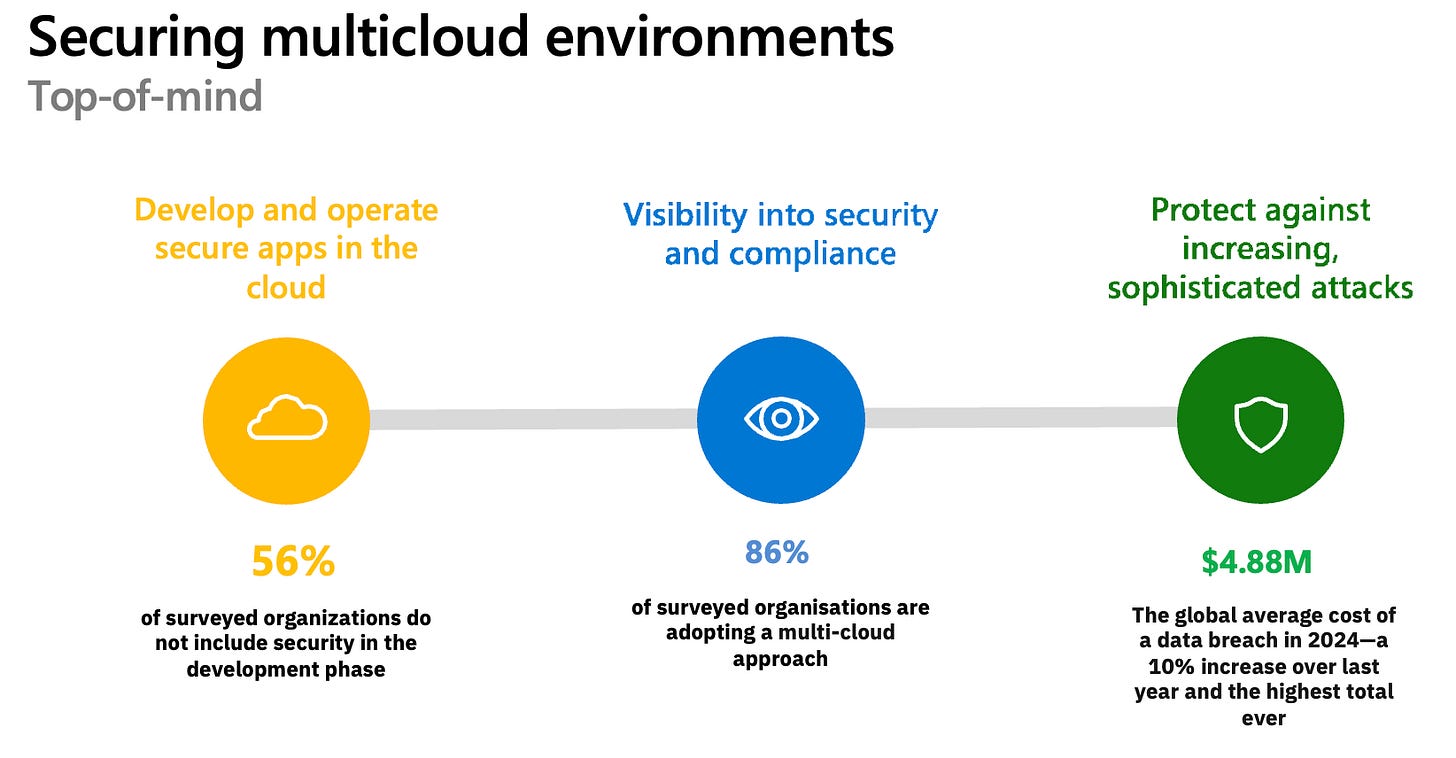
Imagine if a single misconfiguration or unpatched vulnerability could expose millions of customer records in an instant. This isn't a future threat; it's the reality of cloud adoption today. With 86% of organisations adopting a multi-cloud approach, many are struggling to secure cloud-native applications and workloads across their full lifecycle, as highlighted by recent Microsoft data. At the development level, 65% of code repositories contained source code vulnerabilities in 2023, which remained in the code for 58 days on average and 56% of organisations do not include security in the development phase.
The security landscape is evolving rapidly. As companies race to maximise investment and modernise their operations through the cloud, attackers are eager to exploit misconfigurations and poor security practices. In this blog, I’ll examine how Cloud Native Application Protection Platforms (CNAPPs), such as Microsoft Defender for Cloud, can help address these pressing security challenges.
The Evolution of Cloud Infrastructure
In the past, businesses made significant investments in physical servers, data centres, and private networks to handle their applications and workloads. Fast forward to today, and cloud providers like Microsoft Azure enable businesses to instantly deploy infrastructure with just a few clicks or lines of code. Scalability, flexibility, and cost savings are some of the many benefits of Microsoft Azure and other cloud providers.
Key Security Risks in Modern Cloud Development
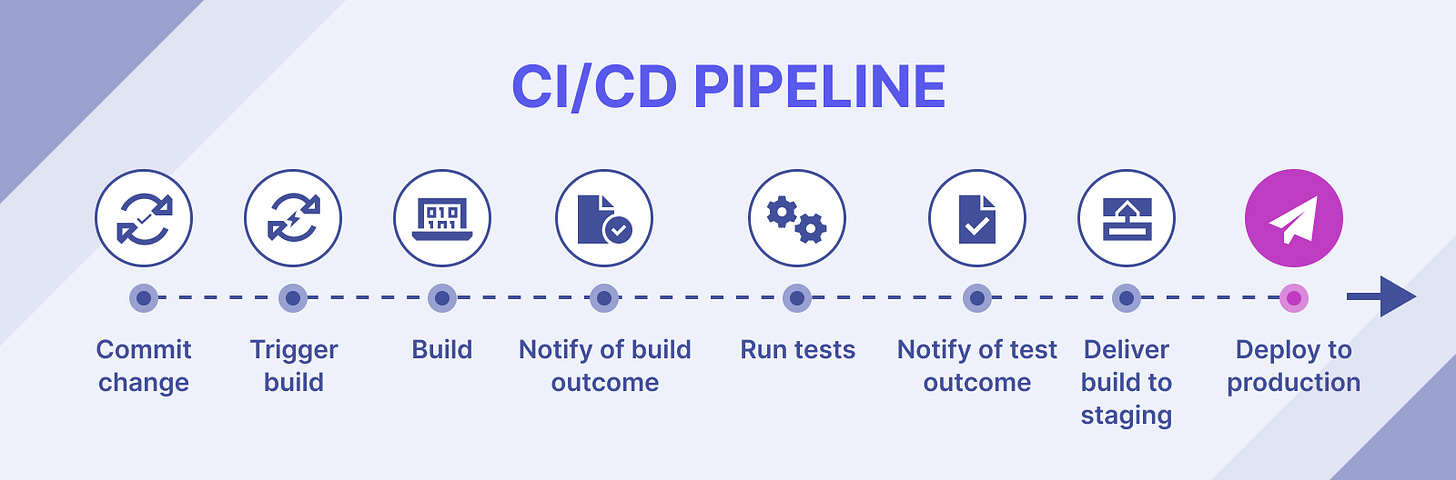
According to Gartner, cloud computing is transitioning from being an innovation driver to a business essential. However, modern application development in the cloud also introduces several security risks. With practices like Continuous Integration/Continuous Deployment (CI/CD), where code is automatically integrated, tested, and deployed rapidly, organisations face unique vulnerabilities that can lead to data breaches. In fact, Gartner predicts that by 2025, 99% of cloud security failures will be the customer’s fault, primarily due to misconfigurations and inadequate security practices.
Common Risks Include:
Misconfigurations: Cloud environments are complex, and misconfigurations can lead to unauthorised access or data breaches. This includes improperly set access controls, open storage buckets, and unsecured APIs.
Overprivileged Access: Granting excessive permissions to users or services can lead to significant security risks if those accounts are compromised.
Vulnerabilities: Applications and services in the cloud can have vulnerabilities that attackers can exploit. These can include outdated software, unpatched systems, and insecure coding practices.
API Security: APIs are often used to connect different services in the cloud, but they can be a target for attacks if not properly secured.
Data Loss and Leakage: Sensitive data stored in the cloud can be lost or exposed due to various reasons, including misconfigurations, insider threats, and inadequate encryption practices.
Lack of Visibility and Monitoring: Without proper monitoring and visibility, it's difficult to detect and respond to security incidents in a timely manner.
Compliance Challenges: Ensuring that cloud applications comply with industry regulations and standards can be challenging, especially as these requirements evolve.
The Limitations of “Standalone“ Cloud Security Solutions:
Existing cloud security solutions often focus on specific areas of the cloud and fail to provide a holistic view of a customer's entire cloud environment these tools are known as “point to point solutions“. The lack of a comprehensive visibility can lead to potential security gaps and vulnerabilities across different aspects of the cloud infrastructure.
As organisations grow and adopt multi cloud strategies along with environments driven by automation, fast release cycles, and modern development practices (like Infrastructure as Code, CI/CD pipelines, containers, serverless functions) the limitations of point to point security tools become more evident.
Organisations tend to end up with a mixture of technologies, with disparate security controls in various cloud environments. This approach leaves them unable to effectively focus, prioritise, and remediate risk, thanks to:
Visibility gaps and security blind spots
Multiple sources of data points, with no single source of truth
Information overflow and time-consuming data correlation processes
Alert fatigue with no indication of critical issues that need attention
Limited resources, technical expertise, and training on each tool
High operational complexity and overhead from managing each tool separately
How CNAPPs Address Cloud Security Challenges
As you can see, rapid cloud adoption introduces numerous risks, and point-to-point security tools struggle to address them comprehensively. This is where CNAPPs come into play. CNAPPs offer unified security management and provide comprehensive visibility across cloud environments, tackling the specific security needs of cloud-native applications.
Cultural Change and the Reality of CNAPP Adoption
While CNAPPs is an effective solution to replace standalone security solutions, addressing their limitations requires more than just technology; it calls for a cultural shift within organisations. From my experience, many customers underestimate the time and cultural shift required when adopting a Cloud Native Application Protection Platform (CNAPP). It's not merely a matter of implementing new tools; it requires a fundamental change in how teams collaborate to enhance the organisation’s security posture.
A very senior colleague once remarked, and I agree, that new processes and programs are often met with resistance. Instead of trying to overhaul everything at once, it’s crucial to work within the existing framework and make incremental improvements. Many customers envision CNAPP as a silver bullet that will magically resolve all their vulnerabilities and security issues.
However, it's important to understand that CNAPP adoption is an ongoing programme of work. It demands continuous management and a well-defined RACI (Responsible, Accountable, Consulted, Informed) framework, involving key business functions. One critical question to ask is: what will you do with the findings once you turn on the solution? Turning on the technology is the easiest part; the real challenge lies in how you act on those findings to improve your security posture.
Microsoft Defender for Cloud: A Leading CNAPP Solution
Microsoft Defender for Cloud offers several key advantages:
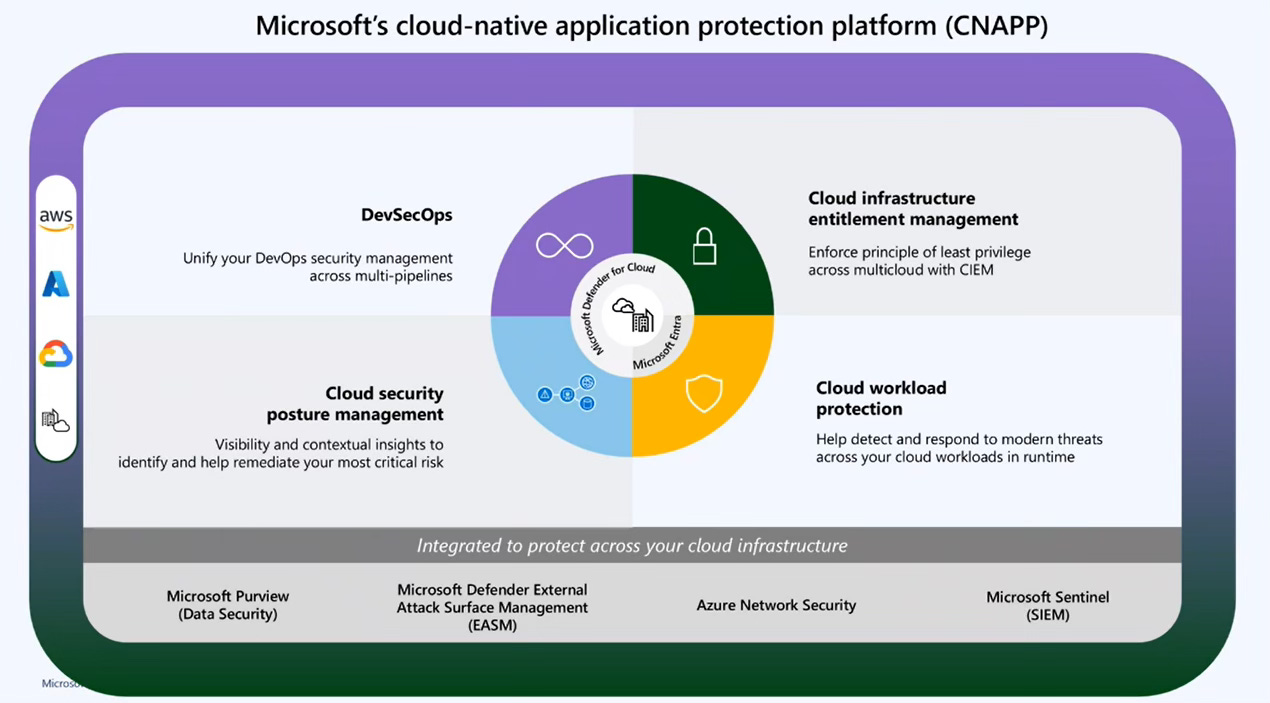
Holistic Security Across Cloud Environments: Defender for Cloud integrates with Azure, AWS, and GCP, providing a unified view for monitoring all cloud services and workloads.
Built-In DevSecOps: It integrates security at the code level within CI/CD pipelines, enabling early detection of misconfigurations and vulnerabilities during development.
Cloud Security Posture Management (CSPM): Defender for Cloud identifies and addresses misconfigurations and compliance issues before they can be exploited.
Cloud Workload Protection Platform (CWPP): It protects individual workloads such as virtual machines (VMs), containers, databases, and serverless functions.
Cloud Infrastructure Entitlement Management (CIEM): Defender for Cloud ensures proper user access controls, reducing risks from insider threats and privilege misuse.
Cloud Service Network Security (CSNS): Secures both internal and external network traffic, protecting cloud infrastructure from network-based threats. CSNS provides enhanced visibility across the network and integrates with Defender for Cloud for real-time threat detection and faster response, ensuring secure and uninterrupted cloud operations.
Benefits of Adopting Defender for Cloud
By integrating Microsoft Defender for Cloud into your security strategy, organisations can enjoy numerous advantages that enhance their overall security posture.
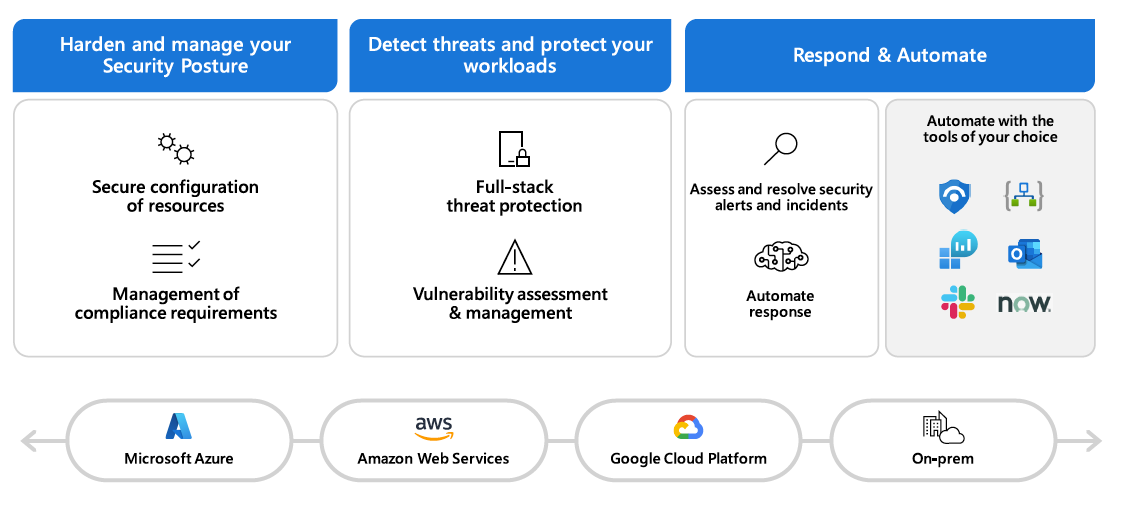
A Single Pane of Glass: Microsoft Defender for Cloud integrates with Azure, AWS, GCP, and CI/CD pipelines, providing a unified view for managing security across multi-cloud environments.
Extended Detection and Response (XDR) Integration: Microsoft Defender for Cloud includes XDR capabilities, offering richer context during investigations.
Reduced Complexity and Overhead: It consolidates multiple security tools into a single platform, reducing the operational complexity of managing different tools.
Comprehensive Cloud and Services Coverage: Defender for Cloud monitors a wide range of services, ensuring visibility across all major cloud platforms.
Security at the Speed of DevOps: Integrated security tools detect and address issues during development and deployment, reducing risks before they reach runtime.
Guardrails to Distribute Security Responsibility: Automated security checks ensure security practices are consistently applied, easing friction between security and development teams.
Continuous Security with CNAPPs
Multicloud security is complex, requiring constant vigilance and adaptation. It's not something that can be addressed with a one-time checklist. Security teams must consistently implement and enforce best practices from the initial stages of development through to runtime, managing identities, access controls, and data protection. This continuous enforcement must span the entire cloud lifecycle and be standardised across all platforms to ensure comprehensive and lasting security.
TLDR:
As organisations rapidly adopt cloud technologies, they face significant security challenges, including misconfigurations and vulnerabilities. Traditional security tools often fall short of providing comprehensive protection in dynamic cloud-native environments. Microsoft Defender for Cloud, a Cloud Native Application Protection Platform (CNAPP), addresses these challenges by offering unified security management, comprehensive visibility, and integrated tools to secure applications throughout their development and deployment lifecycle. Defender for Cloud simplifies cloud security, reduces complexity, and enables faster, more effective responses to threats, making it an essential solution for modern cloud environments.
Dive in deeper with the Uncovering Hidden Risks Microsoft podcast
Have blog ideas, want to engage on a topic, or explore collaboration? Let’s take it offline reach out on LinkedIn. I’d love to connect and continue the conversation!