Defender For Cloud - under the hood: Secure Score Deep Dive
Learn about and discover what the Defender For Cloud Score means and how it helps improve your cloud security posture
If you're measuring your security posture by how many ‘We need to talk’ emails you get from the risk team, it’s time to check your secure score 📧😬. In this blog we’ll explore what the Defender for Cloud secure score is, how it works and how it should be used to get more visibility into compliance and misconfiguration risks.
‼️) This blog is part of a Defender For Cloud "Under the hood series" where we explore the various features, benefits and considerations that come with implementing Defender For Cloud (and other CNAPPs). You don't need any prior experience just a willingness to learn and develop. I don't quite know when the series will end but I hope you enjoy. What is Secure Score?
Secure Score is a simple, at-a-glance percentage that measures your cloud security posture. It’s based on the security controls you're passing and failing, giving you a clear idea of how well your environment is protected. As Microsoft puts it: “The higher the score, the lower the identified risk level.”
Where does secure score come from?
Great question! Secure Score is based on the Microsoft Cloud Security Benchmark (MCSB), an industry best practice framework. According to Microsoft, "Only built-in recommendations from the MCSB affect the Secure Score." This means that while you can configure other compliance standards within Defender for Cloud, they won’t impact your Secure Score. The score is calculated based on security controls from the MCSB and their associated security recommendations.
When you first enable Defender for Cloud, your security posture is measured against the MCSB standard, forming the foundation of your Secure Score.How is Secure Score calculated?
To understand the calculation let’s first understand what a security control is?
In Microsoft Defender for Cloud, a security control is a group of related security recommendations designed to improve your overall cloud security posture. Instead of assessing security fixes individually, these controls bundle them together based on what they protect.
For example, the Microsoft Cloud Security Benchmark (MCSB) as seen above, includes a security control called: NS. Network Security, which has a recommendation stating, "Subnets should be associated with a network security group." Since I’m only partially meeting the recommendations within this control, I won’t receive all the associated points, meaning my Secure Score won’t increase fully. To earn all possible points for a security control, every resource must comply with all the security recommendations within that control.
Here’s the breakdown:
Maximum Possible Score (per control):
Each control has a fixed maximum score (e.g., 6 points). This represents the total value of securing all resources in that category.Total Resources in Scope:
Add up all resources affected by the control’s recommendations (both healthy and unhealthy). Example: 78 resources.Value per Resource:
Divide the control’s max score by the total resources to calculate how much each individual resource contributes:
6 (max score) ÷ 78 (total resources) = 0.0769 points per resourceCurrent Score:
Multiply the “value per resource” by the number of healthy (secured) resources:
0.0769 x 4 (healthy resources) = 0.31 pointsExclusions:
Resources flagged as preview recommendations (experimental or not yet finalised) are excluded from calculations. Only production-ready recommendations count.
Key Takeaways
Controls are weighted: Not all controls contribute equally to your total Secure Score. Critical risks have higher max scores.
Focus on “unhealthy” resources: Fixing a single unhealthy resource adds the same incremental value (0.0769 in the example) to the score.
Aggregate impact: Your total Secure Score is the sum of all individual control scores.
The secure score model incentives prioritising controls with the most unsecured resources or highest max scores. PLEASE REMEMBER just because you get less points for come controls doesn’t mean you can forget about it you should actively work to remediate it.
Inside the console
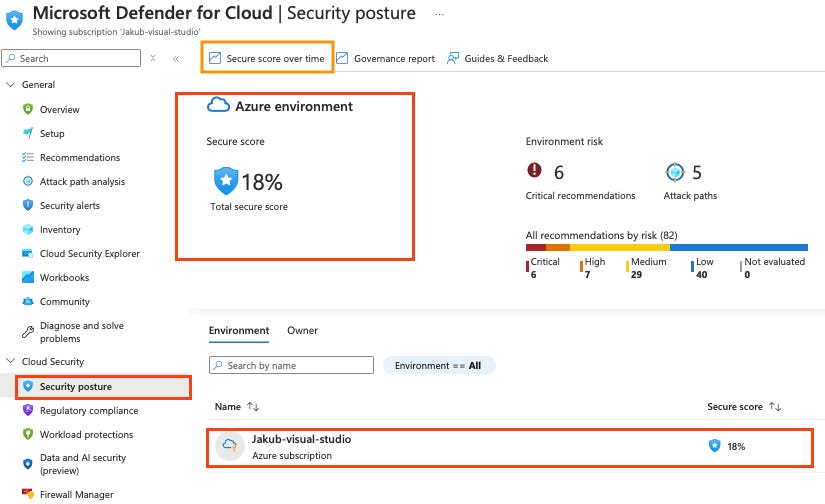
You can view your Secure Score from multiple locations within Defender for Cloud, as well as security recommendations and regulatory compliance standards (which will be covered in another blog). Both the Overview page and the Security Posture page provide a clear view of your score.
Measuring secure score over time:
Although this isn’t a deep dive into workbooks and their use in Defender for Cloud, I wanted to highlight a particularly useful feature Secure Score Over Time. This workbook (drumroll, please) lets you track your security progress by showing the impact of actions you’ve taken to improve your score and reduce your attack surface overtime 🎉.
At the top of the workbook, I can filter results based on a custom time range. The graph on the left displays my past scores, while the right side shows current score trends per scope (in this case, my subscription). My Secure Score is 18% out of 100%, the security controls I’m passing.
Looking at the bottom section of the Secure Score graph, I can see a few key insights, including Top Recommendations with a Recent Increase in Unhealthy Resources. This highlights the recommendations with the most resources that have become non-compliant over time. This is useful because it quickly identifies areas where I should implement preventative guardrails to keep resources compliant and secure.
Why track your secure score?
Tracking changes in your security posture helps you stay on top of what needs attention. Secure Score isn’t about passing or failing! it’s just a way to see if things are improving and taking action.
What affects my secure score?
Your Secure Score changes as new security recommendations are generated when you add resources that don’t comply with security controls from the Microsoft Cloud Security Benchmark (MCSB). As a result, your score may fluctuate based on your environment’s re evaluated security posture. A good way to avoid repeatedly dealing with the same security recommendations such as "Subnets should be associated with a network security group" is to implement preventative guardrails using Azure Policy. This helps ensure resources remain compliant automatically, reducing the need for manual fixes.
To learn about Azure policy check out my other blog: Securing the Cloud with Defender for Cloud and Azure Policy
Where can I view maximum points per control?
You can run the below query in Azure Resource Graph (ARG) to extract the max points per control and your current points please feel free to customise as needed:
// Query to extract Secure Score control details from Microsoft Defender for Cloud (MCSB) along with Subscription ID
securityResources
| where type == 'microsoft.security/securescores/securescorecontrols' // Filter to get only Secure Score controls
| extend
// Extracting control details from the 'properties' field
SecureControl = properties.displayName, // Display name of the security control
Unhealthy = properties.unhealthyResourceCount, // Count of unhealthy resources related to this control
CurrentScore = properties.score.current, // Current score for this control
MaxScore = properties.score.max, // Maximum possible score for this control
SubscriptionId = tostring(subscriptionId) // Add subscription ID to indicate which subscription the control belongs to
| project SecureControl, Unhealthy, CurrentScore, MaxScore, SubscriptionId // Display relevant columns for analysisthe output should look something like this:
From the portal, from the recommendations page click on “classic view“
You’ll then see secure score calculations:
Things to take note of:
Under the hood: Recommendations flagged as Preview aren't included in secure score calculations. You should still remediate these recommendations wherever possible, so that when the preview period ends, they'll contribute toward your score.Under the hood: Defender for Cloud calculates each control every eight hours for each Azure subscription or for each AWS or GCP cloud connector.Under the hood: at this time risk prioritisation doesn't affect the secure score.
Reference:
Defender For Cloud Secure Score
Learn about KQL - A book by Rod Trent Must Learn KQL
Defender For Cloud GitHub Labs
Defender for Cloud Feature requests
Defender for Cloud in the field show
Defender For Cloud Ninja training
Have blog ideas, want to engage on a topic, or explore collaboration? Let’s take it offline reach out on LinkedIn. I’d love to connect and continue the conversation!