Part two: Cloud Security Posture Management (CSPM)
Visibility, Compliance, Control: How CSPM Secures the Cloud
Introduction
In part one of this series on Cloud Native Application Protection Platforms (CNAPPs), we explored the importance of securing cloud environments and the capabilities CNAPPs provide. A key element of cloud security starts with complete visibility into the security and compliance posture of every resource deployed into the cloud. This task is manageable in a single cloud environment, but what if you are using multiple cloud providers?
Relying solely on vendor-specific or third-party point-to-point security solutions can create gaps in visibility, reducing your ability to detect and respond to cloud attacks effectively. When you multiply these tools across various cloud providers, the complexity of managing security increases significantly. In this post, we’ll explore how Microsoft Defender for Cloud’s Cloud Security Posture Management (CSPM) capabilities can help you maintain security and compliance without compromising your cloud adoption.
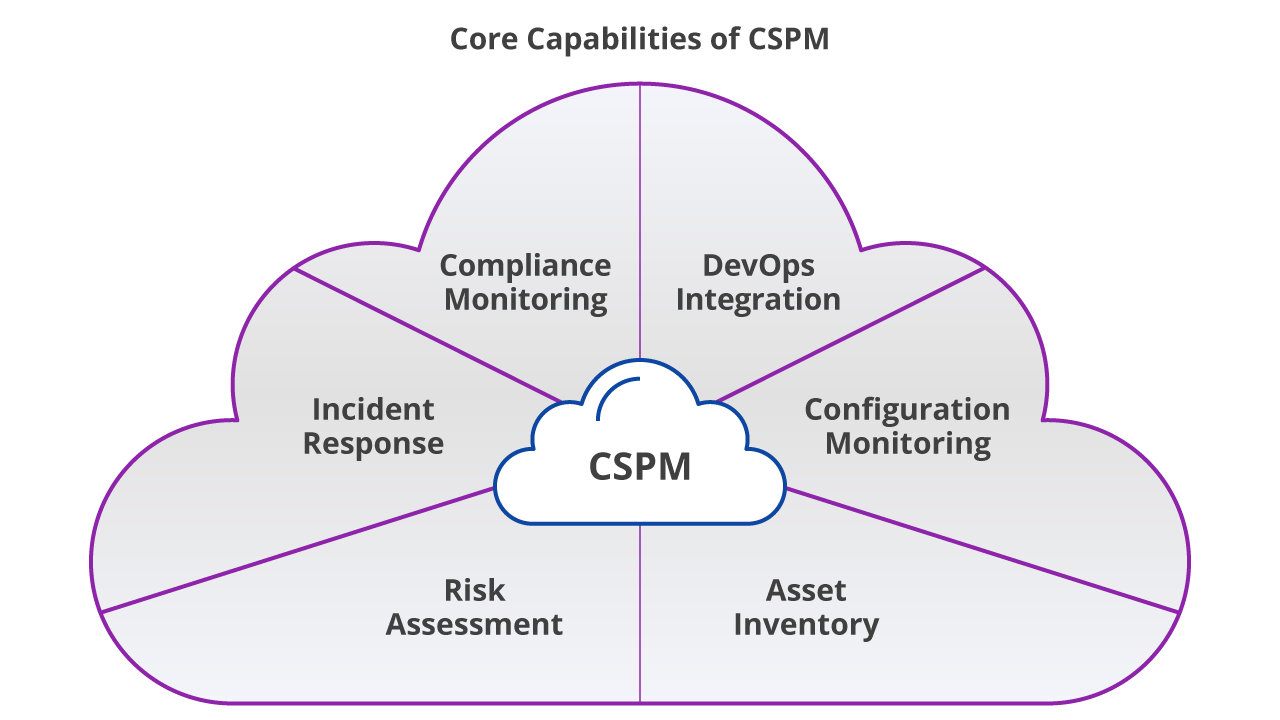
What is Cloud Security Posture Management (CSPM)
CSPM is a strategy to mitigate risks and compliance violations by identifying and remediating misconfigurations across cloud environments. CSPM tools assist security and compliance teams by providing automated visibility, continuous monitoring, and remediation workflows for diverse cloud infrastructure, including Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS).
Why is CSPM important?
While adopting the cloud is beneficial it naturally results in risky cloud configurations, also known as cloud misconfigurations. Cloud misconfigurations can lead to unwanted outcomes including data breaches, fines for violating regulatory compliance and unauthorised access.
A great example of how misconfigurations can be exploited comes from a senior colleague of mine Andrew in one of his blogs, demonstrating how real-world attackers might use scripts or tools like Burp Suite to identify and access unsecured Azure Storage Blobs. His insights underscore the importance of promptly addressing misconfigurations to avoid data exposure risks.
Additionally adopting a multi cloud architecture increases the difficulty of tracking misconfigurations and compliance drifts CSPM tools can detect, unify and normalise cloud provider services into a single console reducing complexity for security teams.
In my experience, customers are often shocked when CSPM tools, like Microsoft Defender for Cloud, reveal the true state of their environments. They expect their configurations to align with vendor and industry best practices, but once the tools are connected, the findings tell a different story. From unexpected misconfigurations to compliance gaps, it's a wake-up call that underscores the importance of continuous monitoring and proactive remediation.
It’s also a wake-up call for organizations to tighten up how functional teams work together to manage these findings. You often discover that certain workloads or subscriptions were previously managed by individuals who have since left the organisation, leaving no one accountable for maintaining the configuration. This lack of ownership can lead to further vulnerabilities, which highlights the need for clear accountability and collaboration across teams to ensure long-term security and compliance.
Let’s look at the data
According to Gartner research:
By 2026, 60% of organisations will see preventing cloud misconfiguration as a cloud security priority, compared with 25% in 2021.
By 2027, 80% of the vendors will offer cloud security posture management (CSPM) as a capability or feature of their cloud security platforms or bundles, compared with 50% in 2022.
40% of organisations used a CNAPP in 2023 and an additional 45% expect to use one by the end of 2024.
86% of organisations embrace multicloud.
82% of breaches involved data stored in the cloud.
54% of organisations do not include security in the development phase.
How does CSPM work?
Connecting your Cloud Environments:
CSPM tools connect to cloud provider APIs for an agentless security to connect you’ll need to grant the required permissions.
Defender for Cloud: Offers both agentless and agent-based security options, providing flexibility in how you secure your cloud environments. You can choose between AWS and GCP clouds for multi cloud deployments and coverage.
Gaining Visibility:
Once connected CSPM provide full visibility into your cloud assets, configurations, audit trails, network communications, and events.
Defender for Cloud: Enhances this visibility by offering a unified view across Azure, AWS, and GCP. It includes features like Security Recommendations for identifying potential issues, a Secure Score for assessing overall security posture, and detailed Security Alerts for real-time monitoring of threats and vulnerabilities.
Identifying Misconfigurations:
CSPM tools use policies and compliance standards to compare configurations against security controls, alerting teams to misconfigurations.
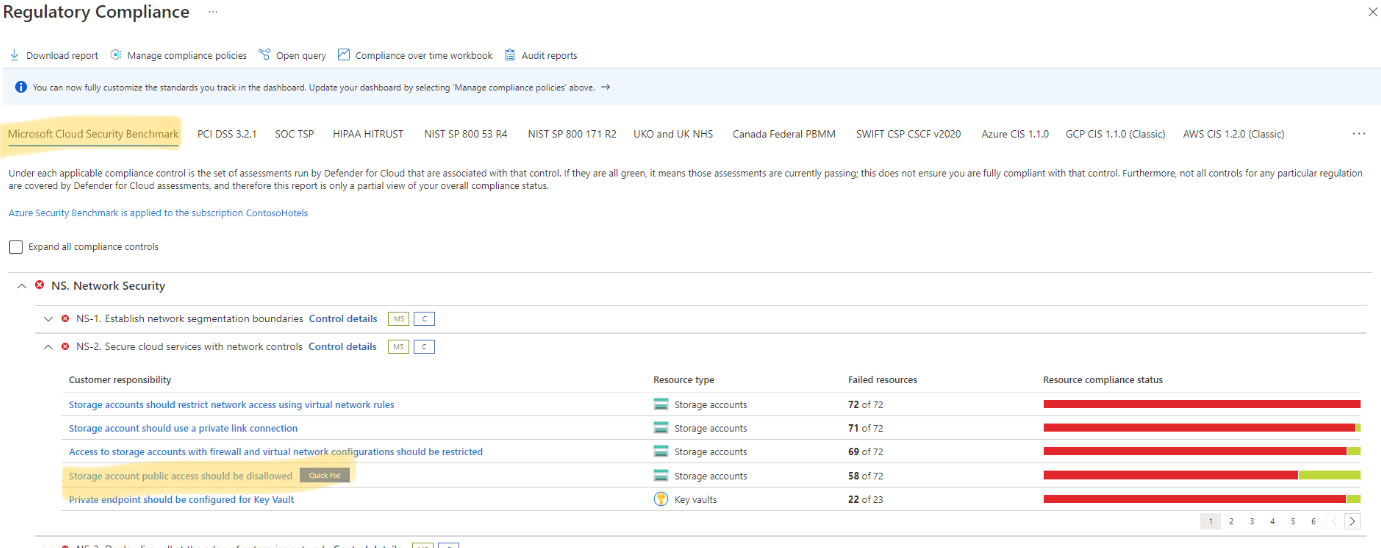
Defender for Cloud: Continuously assesses resources against industry standards and best practices, issuing security recommendations to address misconfigurations. Straight out the box you’ll have the Microsoft cloud security benchmark (MCSB) standard applied.
Detecting Threats:
CSPM tools detect threats using cloud provider telemetry, inspecting logs and events for anomalies and suspicious activity.
Defender for Cloud: Leverages advanced security features across multi cloud environments including: AI & ML algorithms, Microsoft global threat intelligence , behavioural analytics , anomaly detection and when you enable Defender for Cloud, you automatically gain access to Microsoft Defender XDR!
Contextualizing Risks:
CSPM tools contextualise misconfigurations with additional findings, helping prioritise risk based on potential attack paths.
Defender for Cloud: Offers risk prioritization and attack path analysis, helping you understand and prioritize the most critical risks.
Remediating Issues:
CSMP tools offer step-by-step remediation instructions, with some tools providing automated remediation capabilities.
Defender for Cloud: Provides detailed remediation guidance and supports automated remediation to help you address issues efficiently.
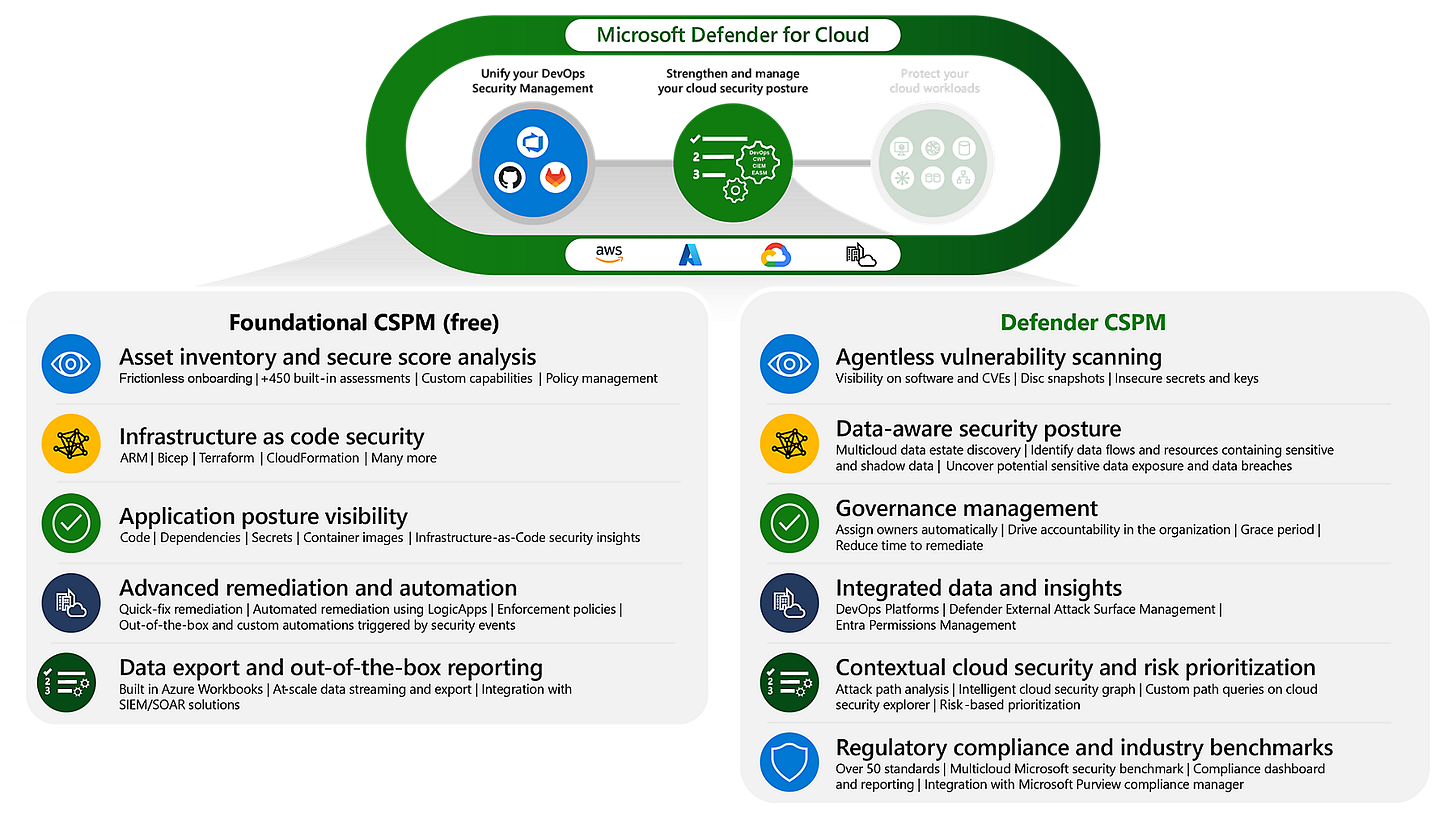
Defender for Cloud CSPM Plan offerings
Defender for Cloud has two offerings:
Foundational CSPM: plan which is the base level of service available for free and turned on by default when you enable Defender for Cloud on your subscriptions and accounts. The plan offers fundamental CSPM capabilities.
Defender Cloud Security Posture Management (CSPM) plan: this plan combines everything in the basic plan and builds on top of that with more advanced cloud security features.
Key Features of the Foundational CSPM Plan
Purpose: Security recommendations in Defender for Cloud form the base and help enhance your security posture by providing actionable steps based on assessments of your resources and workloads.
Security policies: To understand the value of security recommendations in Defender for Cloud its important to understand that security policies in Microsoft Defender for Cloud consist of security standards and recommendations that help to improve your cloud security posture.
A Security standard: defines rules these rules will have compliance conditions in order to meet the rule. If rules cannot be met for whatever reason they are classed as “none compliant“ and the standard will have actions (effects) to be taken if conditions aren't met.
A Security recommendation: Defender for Cloud assesses resources and workloads against the security standards enabled in your Azure subscriptions, Amazon Web Services (AWS) accounts, and Google Cloud Platform (GCP) projects. Based on those assessments, security recommendations provide practical steps to help you remediate security issues.
Mechanism: Microsoft Defender for Cloud, continuously assesses resources and workloads against built-in and custom security standards across your Azure, AWS, and GCP environments. The base plan comes with the Microsoft cloud security benchmark (MCSB) standard applied by default when you onboard cloud accounts to Defender your AWS accounts will also have the AWS Foundational Security Best Practices standard applied. For other security standards, recommendations and regulatory compliance standards (built in and custom) you’ll have to enable the advanced plan. Based on continuous assessments, security recommendations are provided to address identified risks and improve your overall security posture.
Example: A typical security recommendation might suggest enabling encryption for a specific storage account to address potential data exposure risks.
Taking Action: Certain recommendations will have a “quick fix” feature which automatically applies the recommendation others will show manual steps to apply the recommendation.
Functionality: Defender for Cloud maintains a comprehensive inventory of all connected cloud assets, helping you keep track of what’s deployed across your environments. Asset inventory utilizes Azure Resource Graph (ARG), an Azure service that lets you query Defender for Cloud's security posture data across multiple subscriptions to quickly find resources. You can also use KQL if you prefer.
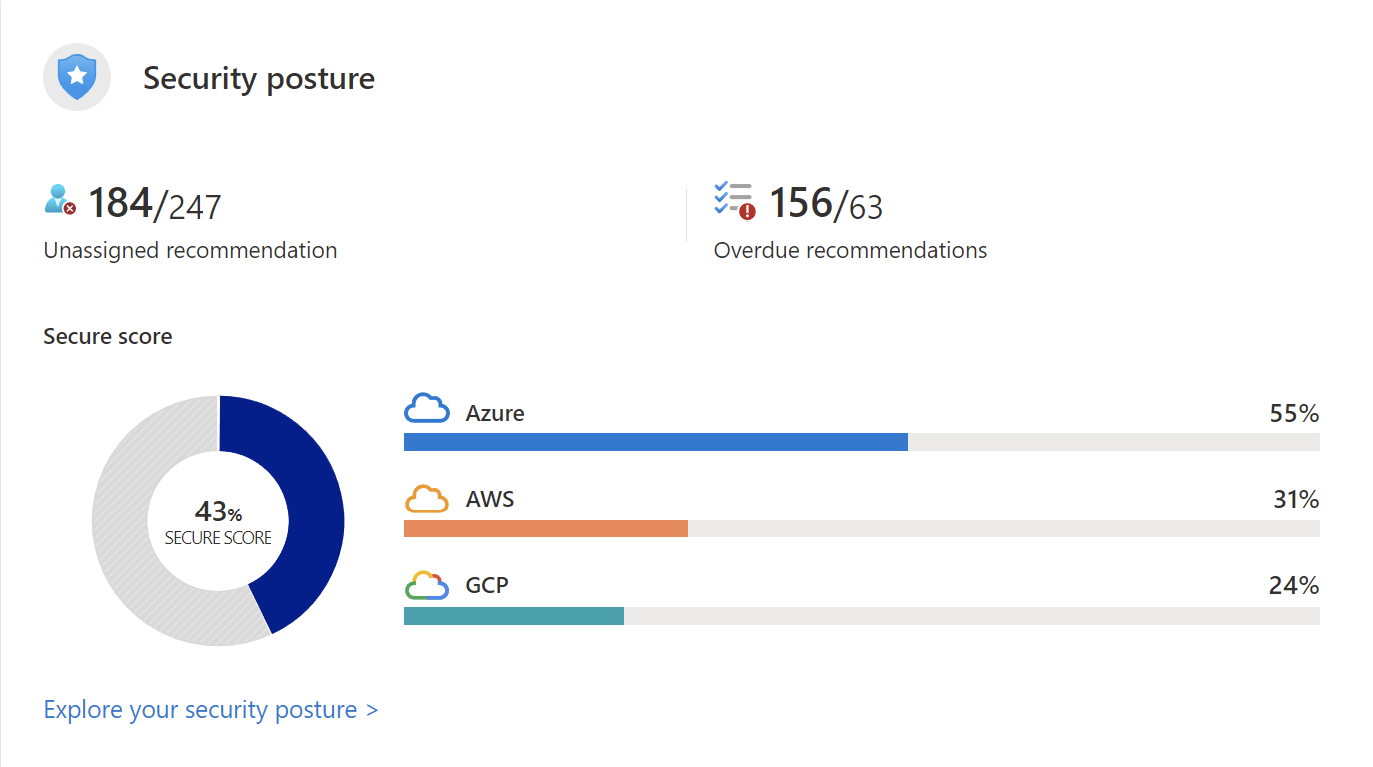
Functionality: The secure score aggregates security findings into a single score so that you can assess, at a glance, your current security situation. The higher the score, the lower the identified risk level is.
Usage: Use the Secure Score to track improvements and identify areas needing attention to enhance your overall security.
Example: When you turn on Defender for Cloud in a subscription, the Microsoft cloud security benchmark (MCSB) standard is applied by default in the subscription. Assessment of resources in scope against the MCSB standard begins. The MCSB issues recommendations based on assessment findings. Only built-in recommendations from the MCSB affect the secure score. Currently, risk prioritisation doesn't affect the secure score.
Data Visualisation and Reporting with Azure Workbooks
Functionality: Azure Workbooks enable you to visualise and report on security data. In Microsoft Defender for Cloud, you can access built-in workbooks to track your organisation’s security posture. You can also build custom workbooks to view a wide range of data from Defender for Cloud or other supported data sources.
Functionality: Defender for Cloud offers various options for exporting security data, which can be useful for compliance and detailed reporting and iterating with third party solutions.
Alert exporting: With the ability to stream security alerts into various Security Information and Event Management (SIEM), Security Orchestration Automated Response (SOAR), and IT Service Management (ITSM) solutions including Microsoft XDR!
Use Cases: Exporting data allows for in-depth analysis and sharing of security information with stakeholders. There are built-in Azure tools that are available that ensure you can view your alert data in the following solutions: Microsoft Sentinel , Splunk Enterprise and Splunk Cloud , Power BI , ServiceNow , IBM's QRadar , Palo Alto Networks , ArcSight.
Functionality: Automate security workflows using logic apps to streamline processes and reduce manual efforts in managing security tasks. For example, you might want Defender for Cloud to email a specific user when an alert occurs. automation might also include notifying relevant stakeholders, launching a change management process, and applying specific remediation steps.
Functionality: Defender for Cloud provides a suite of tools for addressing identified security issues, helping you remediate vulnerabilities effectively. This includes pre created quick fix scripts and logic apps for the fundamental CSPM plan and expands once you enable an advanced plan.
Microsoft Cloud Security Benchmark (MCSB)
Functionality: The MCSB is a set of security standards applied by default in Defender for Cloud, providing a baseline for assessing your cloud security. This benchmark focuses on cloud-centric control areas with input from a set of holistic Microsoft and industry security guidance.
For more details on advanced features, check out the full list here. The full list of advanced features can be found here
TL;DR
CSPM solutions, like Microsoft Defender for Cloud, are crucial for managing cloud security by providing visibility, detecting misconfigurations, and supporting remediation. Adopting CSPM helps mitigate risks and maintain compliance across multi-cloud environments.
Have blog ideas, want to engage on a topic, or explore collaboration? Let’s take it offline reach out on LinkedIn. I’d love to connect and continue the conversation!