Part Six: Cloud service network security (CSNS)
Fortifying networks and enhancing cloud secuirty: How CSNS Defends Against modern threats
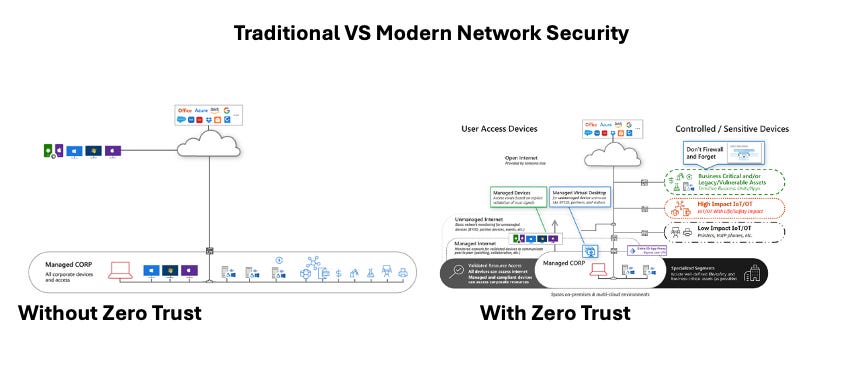
Dissolving Network Boundaries: Embracing Zero Trust with Cloud Service Network Security (CSNS) and CNAPP
In today’s cloud-first world, organisations face over 600 million cyberattacks every day. Traditional network security, designed to protect the now-dissolving perimeter of corporate networks, is struggling to keep up. The rise of remote work, BYOD (bring your own device), and third-party collaborations has blurred the boundaries of corporate networks, making data accessible from anywhere and dramatically expanding the attack surface for cybercriminals.
From my perspective and experience, it’s clear that traditional perimeter-based models simply don’t work in today’s remote and cloud-first world. The shift to decentralised environments, with many moving parts, has significantly complicated network security. This isn’t just a challenge of tools—it’s a challenge of mindset and organisational processes. That’s why adopting a modern approach to network security is no longer optional, but essential.
Why Traditional Security Models Are Failing
According to the Microsoft Digital Defence Report 2024, threats such as ransomware, phishing, and identity attacks thrive in environments where perimeter-based security models assuming anything inside the network is trustworthy are still in place.
The question we need to ask ourselves is: can we afford to keep relying on outdated models while the attack surface grows exponentially? I’ve seen organisations struggle to adapt, and it’s a wake-up call—perimeter security no longer cuts it. What we need is a more resilient model, one that protects every corner of a network, no matter where users, devices, or data reside.
Zero Trust: A New Era of Network Security
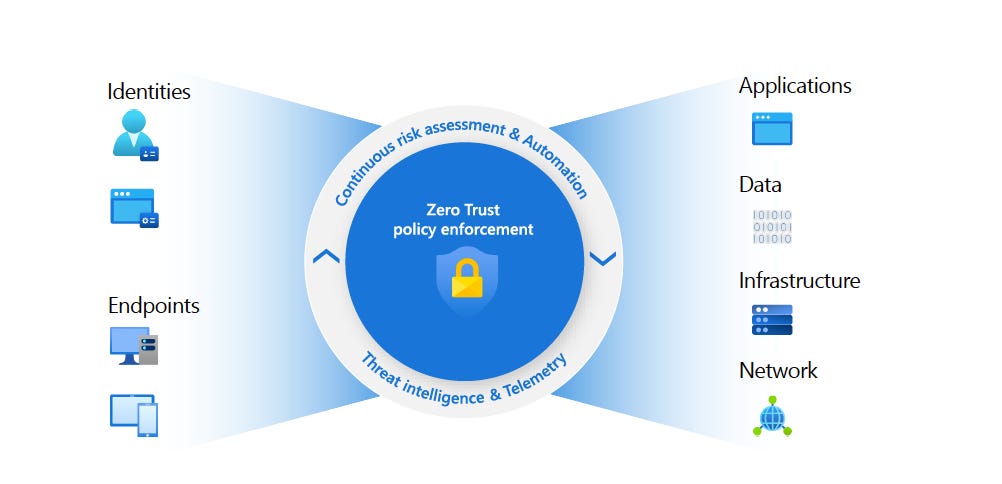
This is where Zero Trust becomes essential, shifting away from implicit trust based on network location to a model where every user, device, and application is continuously verified. In my experience, the biggest challenge with Zero Trust is not the technology—it’s the cultural shift. It requires businesses to adopt a ‘trust no one, verify everything’ approach, which often challenges long-held assumptions about network security.
The Zero Trust model adopts core principles like explicit verification, least-privileged access, and the assumption of breach across multiple domains: Identity, Endpoints, Applications, Network, Infrastructure, and Data. Implementing these principles ensures that even if a network is compromised, attackers cannot move freely within it without breaking through multiple layers of security. Zero Trust isn’t just a buzzword; it’s a fundamental change in how we approach security.
Why the Zero Trust Journey Requires CSNS
Transitioning to Zero Trust is not just a flip of a switch—it requires a strategic, phased journey supported by advanced security solutions. Cloud-Native Application Protection Platforms (CNAPPs) and Cloud Access Security Brokers (CASBs) are essential tools in this journey. In this blog, we’ll explore how Cloud Service Network Security (CSNS) fits into the Zero Trust journey, and why it’s an essential component of modern cloud security.
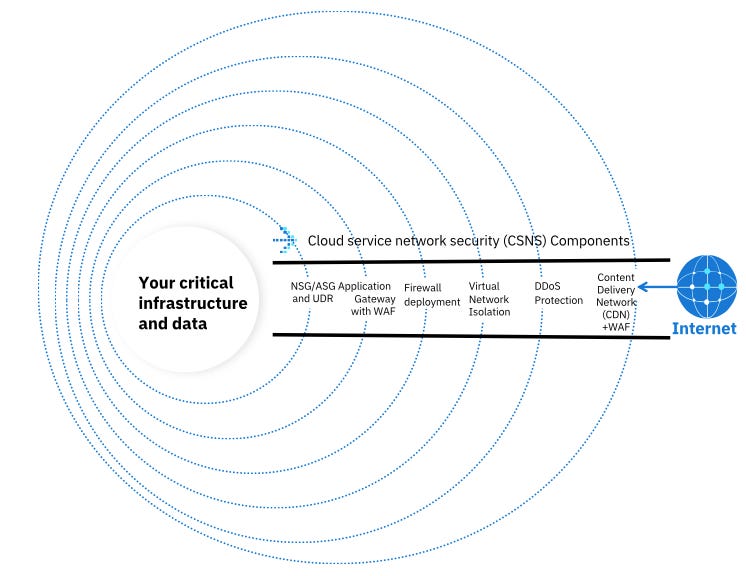
While Cloud Workload Protection Platforms (CWPPs) focus on securing workloads at the application and data layer, and Cloud Security Posture Management (CSPM) helps identify and remediate misconfigurations across cloud environments, Cloud Service Network Security (CSNS) focuses on safeguarding the cloud infrastructure the network that connects workloads, data, and services. This includes preventing distributed denial-of-service (DDoS) attacks, man-in-the-middle (MITM) attacks, and other network-based threats, like the "loop attack”, a new type of attack emerging in 2024 targeting the very protocols that form the backbone of our internet communication.
From my experience, network security is often overlooked until it’s too late. Organisations tend to focus on securing applications and data, but without proper network security, the entire structure is vulnerable. CSNS plays a critical role in preventing lateral movement within a network, making it a cornerstone of a Zero Trust strategy.
A Layered Approach to Network Security
Managing enterprise-scale networks is complex, especially with the numerous entry and exit points (ingress and egress) across cloud environments making them prime targets for attackers. If compromised, these access points can serve as gateways, allowing attackers to move laterally within the network and compromise more critical resources.
Cloud Service Network Security (CSNS) solutions are designed to detect network-based threats early and prevent them from spreading. They often operate in tandem with other security measures, layering protection to ensure maximum coverage and deeper functionality. For example, Microsoft XDR integrates with Azure-native CSNS solutions to provide enhanced detection and faster response times to potential network threats. These technologies are further enhanced by AI, machine learning (ML), and live threat intelligence, delivering real-time threat detection and response.
AI and Network-Based Threats
AI has revolutionised how we approach security, but in my opinion it’s not a silver bullet. While it can analyse vast amounts of network data and detect abnormal behaviour faster than human analysts, I often remind clients and colleagues that AI should complement, not replace, human expertise. It’s also not a "set and forget" solution—AI tools still require continuous tuning and management to deliver effective results. When implemented and managed correctly, AI can significantly enhance your security operations and ease some of the heavy burden on teams.
Taking a look at recent data from the Microsoft Digital Defence Report 2024 reveals that attackers are increasingly using AI to automate vulnerability identification and execute attacks at an unprecedented scale. Groups like Forest Blizzard (STRONTIUM) and Emerald Sleet (THALLIUM) are leveraging AI for reconnaissance and social engineering, underscoring the urgency for businesses to adopt AI-driven defences.
The good news is that vendors like Microsoft are advancing their AI-driven innovations. For example, Microsoft’s AI-powered threat intelligence network processes over 78 trillion cybersecurity signals per day, providing organisations with the data they need to stay ahead of increasingly sophisticated threats. When used properly, AI proves to be invaluable in this context; there simply aren't enough analysts to manually analyse that volume of signals. This data also feeds into Microsoft XDR and threat analytics reports, which threat analysts use daily to assess how these threats may impact an organisation.
Where does Cloud Service Network Security (CSNS) fit into CNAPP?
While Cloud Service Network Security (CSNS) isn’t always listed as a core component of Cloud-Native Application Protection Platforms (CNAPPs), it plays an essential role in securing cloud-native environments. CSNS ensures the security of both external traffic and internal communications within the cloud infrastructure, complementing the protections offered by Cloud Workload Protection Platforms (CWPPs) and Cloud Security Posture Management (CSPM).
In my earlier blog, "The Value of a Cloud Native Application Protection Platform (CNAPP)," I explored how CNAPPs address challenges like misconfigurations and vulnerabilities. As organisations adopt multi-cloud strategies, the role of CSNS becomes even more crucial, providing the network security layer that CNAPPs need to offer comprehensive protection.
Key Azure CSNS Solutions and Their Integration with Defender for Cloud
All major cloud providers—including Microsoft Azure, AWS, and Google Cloud Platform (GCP) offer their own CSNS solutions. Microsoft Azure’s CSNS solutions integrate with Defender for Cloud and the wider Microsoft XDR eco system to deliver intelligent, automated, and integrated security across domains. Enhancing overall cloud security as part of a robust CNAPP platform.
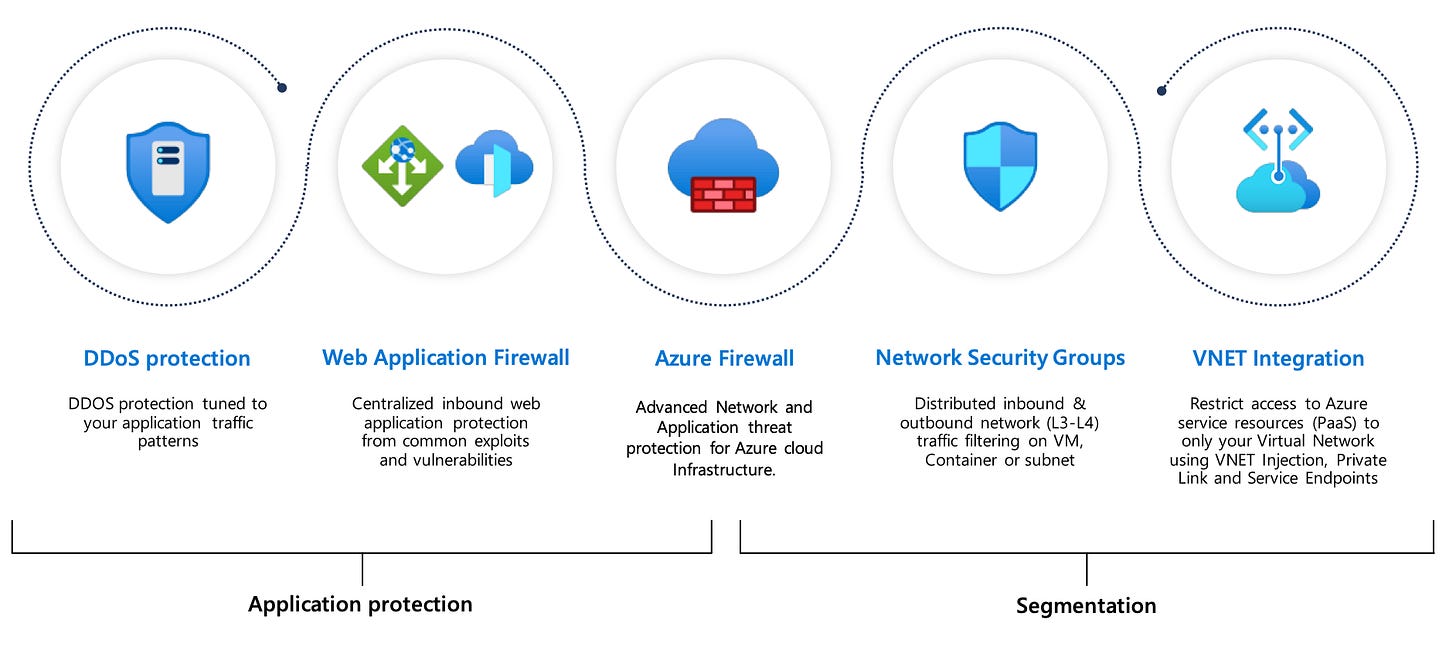
Just-in-Time (JIT) VM Access: Limits the exposure of sensitive ports (RDP, SSH) to reduce attack surfaces. Defender for Cloud monitors these requests and flags suspicious activity.
Network Map: Visualises the network topology, helping to identify exposed endpoints and misconfigurations. Integrated with Defender for Cloud for actionable insights.
DDoS Protection: Azure DDoS Protection shields applications from large-scale attacks. Defender for Cloud assesses DDoS configurations and alerts on potential threats. Microsoft Defender for Cloud provides a list of security alerts, with information to help investigate and remediate problems.
Web Application Firewall (WAF) Monitoring: Application Gateway WAF is integrated with Microsoft Defender for Cloud. Defender for Cloud provides a central view of the security state of all your Azure, hybrid, and multicloud resources.
Azure Firewall Integration: Monitors traffic filtering rules, ensuring that Azure Firewall is configured to minimise risk. WAF alerts are streamed to Defender for Cloud with no other configurations.
Private Link Monitoring: Protects data by restricting traffic to private endpoints, preventing exposure to the public internet. You can monitor this security baseline and its recommendations using Microsoft Defender for Cloud.
Each of these solutions enhances the security of cloud networks by integrating with Defender for Cloud, which provides continuous monitoring and real-time alerts. By leveraging CSNS with CNAPP , organisations can significantly reduce the risk of network-based attacks while gaining deeper visibility into their cloud environment all from a single pane of glass.
EXTRA RESOURCES
Although this blog didn’t delve deeply into the complexities of adopting Zero Trust, it highlighted how a critical component of CNAPP, Cloud Service Network Security (CSNS), supports this journey. The path to embracing Zero Trust is indeed challenging and requires significant changes across an organisation.
I plan to revisit the Zero Trust topic in future blogs, as it is a rich area for exploration that offers new insights at every turn. It's a complex subject that can't be fully covered in a single post. To further your understanding of Zero Trust, here are some valuable resources:
TLDR
As organizations face over 600 million cyberattacks daily, traditional perimeter security is no longer enough. Zero Trustand Cloud Service Network Security (CSNS) are key components of modern cloud security, helping safeguard networks and data by continuously verifying access and detecting threats in real time. Integrating AI-driven solutions and leveraging 78 trillion threat signals per day, CSNS strengthens organisations' defences against sophisticated attacks. Combined with CNAPP, these technologies ensure visibility and protection across cloud environments.
Have blog ideas, want to engage on a topic, or explore collaboration? Let’s take it offline reach out on LinkedIn. I’d love to connect and continue the conversation!