Part Four: Securing Cloud Workloads Why CWPP is Essential in the Cloud-First Era
Detect, Defend, Secure: the importance of CWPP for Modern Cloud Workloads
The Rapid Shift to Cloud: What it Means for Workload Security
In today's cloud-first world, a simple misconfiguration in a database or serverless function can leave your business vulnerable to cyberattacks. With cloud adoption accelerating, Cloud Workload Protection Platforms (CWPP) have become indispensable for securing cloud environments.
According to Gartner, 65% of application workloads will be optimal or ready for cloud delivery by 2027, up from 45% in 2022. Further to that, Cloud Will Become a Business Necessity by 2028 as cloud adoption accelerates, so too does the risk of cloud-native malware infections—malware designed specifically to exploit vulnerabilities in cloud infrastructure or spread through cloud-native applications and tools. This growing risk underscores the need for a comprehensive unified approach to cloud security.
Why Traditional Workload Security Solutions Fall Short in the Cloud
As discussed in my previous blog posts, existing cloud security solutions often focus on specific areas of the cloud and fail to provide a holistic view of an entire cloud environment these solutions are known as 'point-to-point solutions'.
many companies rely on individual vendors to manage specific parts of their workload protection. The lack of a comprehensive visibility can lead to potential security gaps and vulnerabilities across different aspects of the cloud infrastructure. When cloud workloads span across multiple cloud environments, a larger, more complex attack surface is created.
Organisations tend to end up with a mixture of technologies in a scramble to protect their cloud environments, this approach leaves them unable to effectively focus, prioritise, and remediate risk, thanks to:
Visibility gaps and security blind spots
Multiple sources of data points, with no single source of truth
Information overflow and time-consuming data correlation processes
Alert fatigue with no indication of critical issues that need attention
Limited resources, technical expertise, and training on each tool
High operational complexity and overhead from managing each tool separately
Traditional security tools, while once effective simply cannot keep up with the dynamic and fast-paced nature of modern cloud workloads. These issues illustrate the need for a more integrated approach, which brings us to Cloud Workload Protection Platforms (CWPP) a central pillar of Cloud Native application protection platforms (CNAPPs).
Cloud Workload Protection Platforms (CWPP): The Future of Cloud Security
So, what exactly is a Cloud Workload Protection Platform? (CWPP) it's a security solution created to address the unique security requirements of diverse compute workloads in cloud environments - databases, VMs, serverless functions, APIs, containers and so on. Each compute workload requires its own flavour of protection – there isn’t a 'one-size-fits-all' solution therefore a 'workload centric stack' is required which meets the security requirements of a workload.
Every cloud workload presents potential attack vectors if not adequately secured regardless of usage frequency, operational workloads can be targeted by attackers. Traditional point-to-point security solutions often create visibility gaps and slow response times this is where CWPP shines.
With CWPP, workloads are continuously protected during both normal operations and transitional stages (when workloads are being moved or modified). CWPP integrates seamlessly with XDR (Extended Detection and Response), SIEM (Security Information and Event Management), and SOAR (Security Orchestration, Automation, and Response) tools such as Microsoft XDR and Microsoft Sentinel, providing central visibility across multi-cloud environments.
How CWPP Secures Workloads: Key Features Explained
A Cloud Workload Protection Platform such as Microsoft Defender for Cloud combines multiple security components depending on the workload being protected*:
Vulnerability management: Actively scans the applications and software running on your workloads to find misconfigurations and flag vulnerabilities which could be exploited if not properly addressed. This feature can also be used to scan your workloads before they are published both internally and externally.
Runtime protection: Involves monitoring and protecting workloads as they run in the cloud computing environment, defending against attacks, malware and unauthorised activities in real time. Defender for Cloud integrates with Defender for Endpoint to automatically scan, detect, respond and remediate potential threats running on workloads. As an additional benefit, Defender for Endpoint is fully integrated with the Microsoft XDR suite.
Container Image Analysis: For containerised environments, Defender for Cloud inspects container images for security risks, including outdated packages, vulnerabilities or embedded malware, before they enter production. You can define and enforce policies around trusted registries, repositories, and images to ensure that only verified and authorised components are used in deployments.
Consistency Across Cloud Environments: Microsoft Defender for Cloud ensures consistent application of security policies and controls across all cloud platforms, including AWS, Google Cloud Platform, Microsoft Azure, and even on-premises environments. This standardisation strengthens your security posture across different infrastructures.
Compliance Management: Defender for Cloud ensures cloud workloads align with regulatory standards such as PCI DSS, HIPAA, and GDPR. It continuously assesses your environment against predefined regulatory controls, helping organisations maintain compliance and reduce the risk of non-compliance.
Workload Hardening: Defender for Cloud offers tailored security recommendations for hardening cloud workloads by identifying and mitigating potential risks across virtual machines, containers, databases, and other cloud resources.
API Security: Defender for APIs in Microsoft Defender for Cloud offers full lifecycle protection, detection, and response coverage for APIs.
Defender for APIs helps you to gain visibility into business-critical APIs. You can investigate and improve your API security posture, prioritize vulnerability fixes, and quickly detect active real-time threats.
Unified Multi-Cloud Security with Microsoft Defender for Cloud and Microsoft XDR
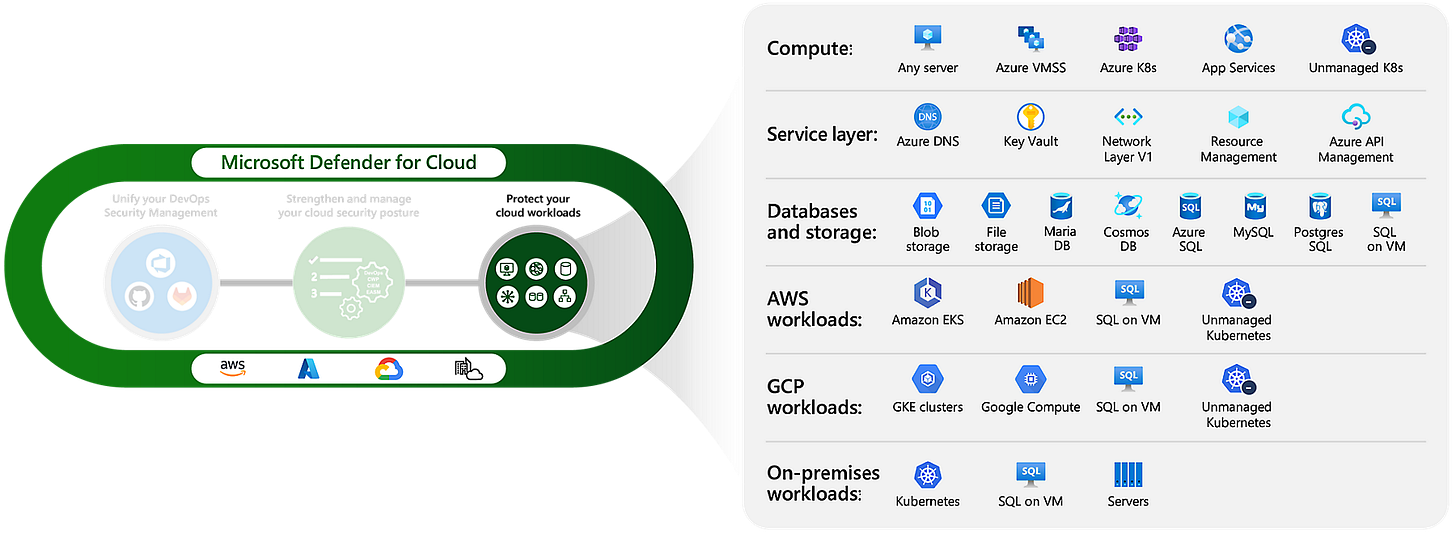
Cloud Workload Protection Platforms (CWPP), such as the one offered through the Microsoft Defender for Cloud CNAPP solution, protect a wide variety of workloads across multi-cloud environments. The diagram below references all types of workloads you can protect the pricing can be viewed here as it differs per workload.
The most common workloads you can secure across vendors:
Virtual Machines (VMs): From traditional VM-based workloads running in Azure, AWS, or GCP, CWPP ensures security configurations, compliance, and runtime protection.
Containers: In containerized environments, such as those using Kubernetes, CWPP provides continuous monitoring of container images for vulnerabilities and ensures security policies are enforced at runtime.
Serverless Functions: Serverless workloads (e.g., Azure Functions, AWS Lambda) are also a key focus. CWPP helps secure them by monitoring access controls, enforcing runtime protection, and identifying potential risks.
Databases: CWPP ensures that databases running in the cloud, such as Azure SQL, AWS RDS, and others, are protected from unauthorized access, vulnerabilities, and misconfigurations.
APIs: Defender for Cloud includes protections for APIs, securing the interfaces through which many cloud-native applications operate, ensuring proper access control and visibility into potential threats.
The specific workloads you can protect will vary slightly between vendors, but the core concept of securing databases, VMs, containers, and APIs remains consistent across all major platforms.
Microsoft XDR & Defender for Cloud Integration
As mentioned earlier Defender for Cloud fully integrates with Defender XDR and is a central component of the Microsoft Defender XDR suite. Any Defender for Cloud alerts and incidents have been seamlessly integrated into the Microsoft Defender XDR portal. This facilitates a comprehensive investigation experience that includes cloud resources, devices, and identities.
This crucial integration extends the scope of detection and investigation capabilities to include cloud entities. It also enhances the operational efficiency of security teams and enriches the investigative context across the digital spectrum of an organization.
The integration guarantees the elimination of duplicate incidents or alerts across Defender workloads, ensuring each incident is unique and accurately represented. It achieves an automatic correlation of alerts and incidents, weaving together detailed attack narratives and providing security teams with a complete overview of potential threats.
The Business Value of CWPP: Boosting Security and Compliance
Adopting a CWPP solution can significantly transform both your cloud security posture and business operations. Here’s how:
Visibility: CWPP offers unparalleled visibility into workloads across AWS, GCP, and Azure, eliminating blind spots and providing real-time insights into vulnerabilities and threats. With a unified dashboard, security teams can easily identify, prioritise, and act on security issues across multi-cloud environments, reducing reaction times and improving efficiency.
Compliance: Organizations face strict regulatory requirements like PCI DSS, GDPR, and HIPAA. CWPP, integrated with Cloud Security Posture Management (CSPM) in tools like Defender for Cloud, ensures continuous monitoring of compliance across all workloads, reducing the risk of fines and audit failures by automating compliance checks.
Improved Cloud Security Posture: CWPP is instrumental in strengthening your overall cloud security posture. With features like continuous vulnerability scanning, runtime protection, and CI/CD pipeline integration, CWPP enables security teams to proactively protect workloads at every stage of the lifecycle. This continuous oversight, combined with automated remediation and integrated DevSecOps practices, ensures that your cloud environments remain secure.
CWPP vs CNAPP vs CSPM: Understanding the Differences and Benefits
While Cloud Workload Protection Platform (CWPP), Cloud Security Posture Management ( CSPM) and Cloud-Native Application Protection Platform (CNAPP) focus on securing cloud workloads, they differ in scope:
CWPP: Specialises in protecting individual workloads (VMs, containers, databases, serverless functions, APIs) with targeted features.
CSPM: Cloud Security Posture Management (CSPM) focuses on continuously monitoring and assessing cloud infrastructure for misconfigurations, security risks, and compliance issues. CWPP, on the other hand, protects individual workloads such as VMs, containers, and serverless functions. Together, they form a layered defense, with CSPM securing the overall cloud environment and CWPP safeguarding the workloads within it.
CNAPP: Offers a broad security stack that includes CWPP functionality and integrates multiple other security components providing end-to-end protection from code development to runtime operations:
TL;DR
The shift to cloud-native environments requires a new approach to security—one that traditional tools simply can't offer. As cloud adoption accelerates and workloads diversify, CWPP is no longer optional; it’s a critical component of any effective cloud security strategy. Failing to implement a solution like Microsoft Defender for Cloud could leave your workloads—and your business—vulnerable to increasingly sophisticated attacks.
Have blog ideas, want to engage on a topic, or explore collaboration? Let’s take it offline reach out on LinkedIn. I’d love to connect and continue the conversation!