Part Five: Cloud infrastructure entitlement management (CIEM)
Why Identity Management Matters in Cloud Environments: Securing Human and Machine Identities
Why Identity Management Matters in Cloud Environments
What makes cloud infrastructure more complex than it already is? securing, managing and governing identities (human and machine) across multi-cloud environments. The challenge is compounded by the need to ensure these identities are not exploited or abused.
Two recent high-profile security incidents the Okta October 2023 breach and the 2024 Midnight Blizzard espionage campaign—underscore a common vulnerability: overprivileged and poorly managed access entitlements within cloud infrastructures. Although the attack methods differed, the lesson is clear securing identities and entitlements in the cloud is now more complex and critical than ever. In this blog, we’ll explore how Cloud Infrastructure Entitlement Management (CIEM) can be a game-changer for securing identities.
The Growing Complexity of Cloud Environments and identity sprawl
According to Microsoft’s 2023 State of Cloud Permissions Risks report, the data is alarming:
Workload identities now outnumber human identities 10:1 double that of 2021. This significant uptick introduces new security risks.
More than 80% of workload identities are inactive, double the percentage reported in 2021.
More than 70% of identities have not used any of their permissions granted in the last 90 days.
Workload identities are using less than 5% of their granted permissions.
More than 70% of identities are Super Admins
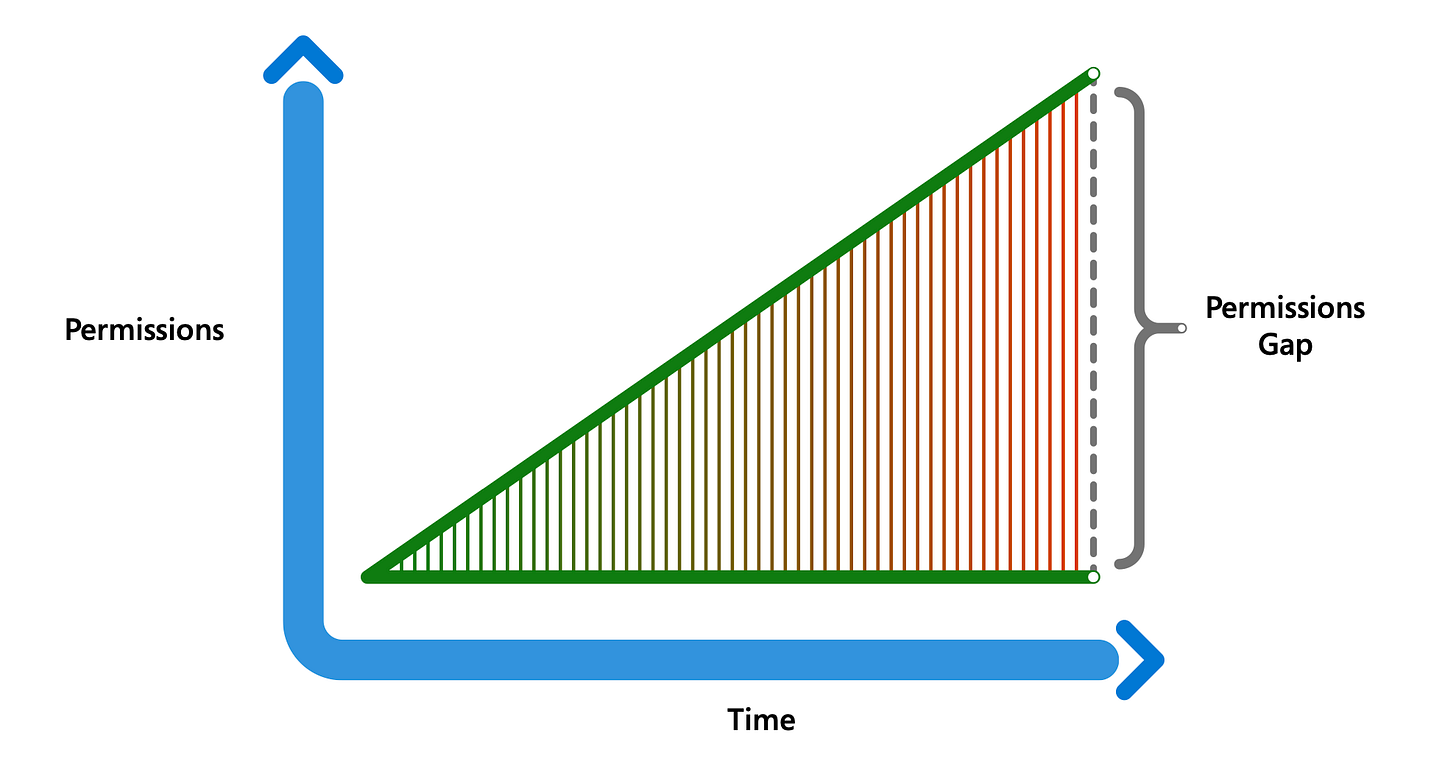
As multi-cloud environments grow, managing permissions becomes a critical challenge. Today’s cloud infrastructures offer over 40,000 possible permissions, with more than 50% classified as high-risk. This complexity makes it increasingly difficult for organisations to track who has access to sensitive data, raising the risk of data breaches and service disruptions.
The rapid growth of workload identities, which now outnumber human identities by 10:1, is particularly concerning. Many of these identities are inactive or over-permissioned, creating blind spots that attackers can exploit. On average, only 1% of granted permissions are actively used, leaving a massive permissions gap that heightens security risks.
Lessons from experience
Drawing on insights from my professional experience, I have found that regular permission reviews are crucial yet frequently neglected due to a lack of clear processes and automation. This challenge intensifies in complex multicloud and on-premises environments, where managing permissions at scale can become overwhelming.
When roles and responsibilities are not clearly defined, permission management can devolve into chaos. Establishing role personas is essential for addressing permission creep. In my observations, organisations often struggle significantly when they lack well-defined role personas and appropriate functional permissions. Therefore, collaborating with department heads and managers to assess necessary permissions is critical; this groundwork facilitates the implementation of Zero Trust and least privilege principles.
Additionally, maintaining an organised list of workload and subscription owners is vital. Having clarity regarding responsibilities helps prevent confusion and enables owners to articulate the roles or permissions required for their tasks. Participation in governance meetings related to assigned permissions is equally important to ensure alignment and identify potential issues early.
Moreover, it is imperative to monitor permission drift and track the usage of high-privilege roles. By implementing alerts to notify relevant teams when these roles are accessed, organisations can enable swift action to uphold security and mitigate unauthorised access.
The Joiners, Movers, Leavers (JML) process should not be overlooked. Automating this process and integrating it with HR systems is essential. Prompt updates to permissions when employees transition between departments or leave the organisation are crucial for minimising the attack surface.
Lastly, establishing alerts and monitoring applications and service accounts that utilise high-privilege delegated permissions is critical. This vigilance aids in the early detection of suspicious activity, thereby enhancing the overall security posture. Cloud Infrastructure Entitlement Management (CIEM) can significantly alleviate the burdens associated with these challenges by providing the necessary tools and frameworks for effective identity and permission management.
What Is CIEM?
Cloud Infrastructure Entitlement Management (CIEM) helps address the challenges of managing overprivileged identities. CIEM solutions, such as Microsoft Entra Permissions Management, provide a structured and automated approach to managing identities and permissions in cloud environments. The goal? To understand which access entitlements exist, then identify and mitigate risks resulting from excessive or unnecessary permissions.
CIEM doesn't just manage access to cloud infrastructure (like storage and compute resources). It also applies to all types of access entitlements, including application services and APIs. CIEM covers both human users and machine identities running in cloud environments.
CIEM addresses three specific categories of entitlements:
Resource-level entitlements: Define functional tasks, such as reading or writing data or setting up virtual machines.
Service-level entitlements: Grant operational privileges like starting or stopping VMs or cloning databases.
Management-level entitlements: Define administrative rights, such as configuring security settings or creating cloud accounts.
How CIEM Tools like Microsoft Entra Permissions Management work?
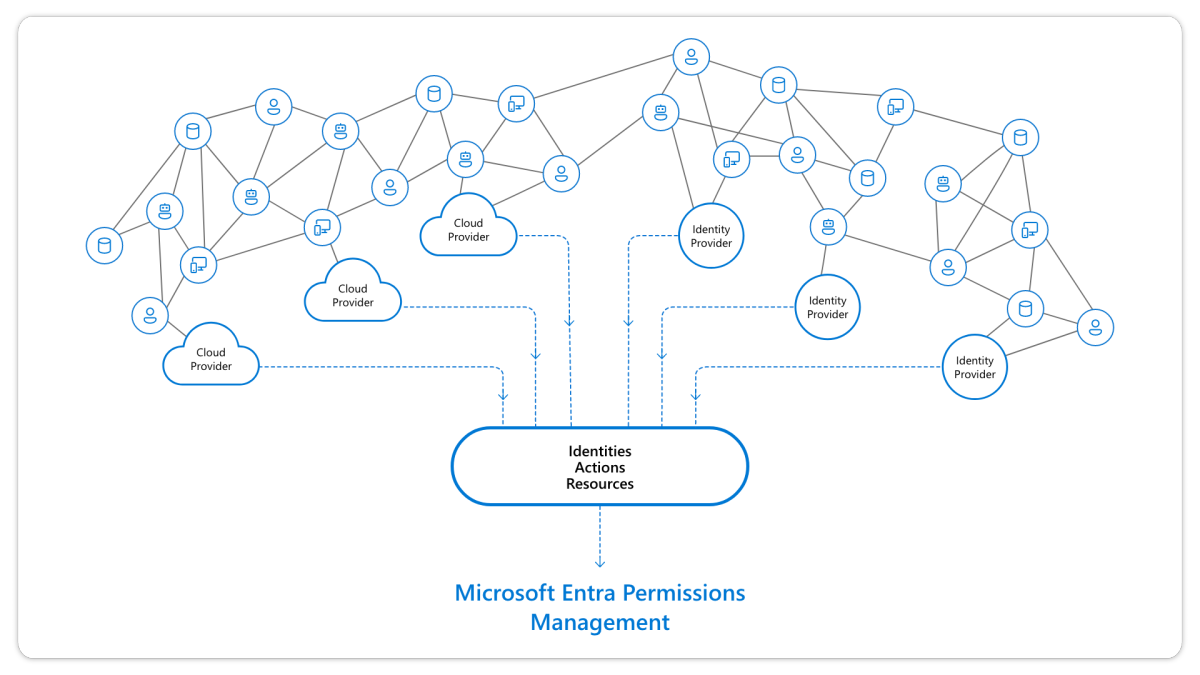
With CIEM, organisations can continuously discover, remediate, and monitor the activity of every unique user and workload identity operating in the cloud. By managing permissions consistently across clouds and enforcing the principle of least privilege for all identities, organisations will reduce their permissions gaps and get one step closer to achieving Zero Trust.
Entitlement Visibility (Discover): To manage cloud permissions effectively, the first crucial step is gaining visibility into existing entitlements. CIEM solutions automatically scan access control policies, rules, and configurations to identify which human or machine users have access to which cloud resources. With Entra Permissions Management you’ll get:
Cross-cloud permissions discovery for AWS, Azure, and GCP.
Permission Creep Index (PCI) to measure the risks of unused or excessive permissions.
Permission usage analytics that provide a multi-dimensional view of risk across identities, actions, and resources.
Rightsizing Permissions (Remediate): Once entitlements are identified, CIEM tools assess whether the access granted is limited to what’s necessary for the workload’s purpose. If excessive privileges are found, administrators are alerted, or permissions can be automatically adjusted. With Entra Permissions Management you’ll also get:
Automated deletion of permissions unused for 90 days.
Permissions on-demand for time-limited access when needed.
Analytics using AI & ML (Monitor): CIEM tools use advanced analytics, including machine learning and User and Entity Behavior Analytics (UEBA), to dynamically assess whether entitlements are appropriately aligned with current workload needs. This allows for real-time adjustments, such as removing entitlements associated with inactive or departed user identities. With Entra Permissions Management you’ll also get:
ML-powered anomaly detections.
Context-rich reports around identities, actions, and resources to support rapid investigation and remediation.
CIEM vs CSPM
While Cloud Security Posture Management (CSPM) tools assess cloud configurations to identify risks, CIEM focuses specifically on access entitlements. CSPM identifies general cloud configuration mistakes, while CIEM evaluates permissions at a granular level to mitigate risks related to over-permissioned identities.
CIEM vs IAM
entity and Access Management (IAM) focuses on managing user identities and permissions across IT resources but isn't designed for the dynamic nature of cloud environments. CIEM, on the other hand, is built for the cloud, providing deeper visibility and control over cloud-specific permissions and risks like permission spraw.
CNAPP vs CIEM
A Cloud-Native Application Protection Platform (CNAPP) secures cloud-native applications throughout their entire lifecycle—from development to runtime—by integrating security across workloads, identities, and configurations. It focuses on securing cloud workloads, containers, and applications in multicloud environments. CIEM, on the other hand, is specifically designed to manage cloud permissions and entitlements, reducing access risks. When integrated with CNAPP, CIEM enhances cloud security, providing a comprehensive, end-to-end solution.
Okta October 2023 Breach: How CIEM Could Have Helped
The Okta breach revealed how attackers can leverage overprivileged admin roles and exploit insufficient entitlement controls. With a robust CIEM solution in place, the excessive permissions granted to key accounts could have been detected early, limiting the potential damage.
How CIEM could have helped prevent the attack:
CIEM automatically detects over-permissioned identities and flags excessive privileges.
It ensures least privilege access by right-sizing permissions, thereby reducing attack surfaces.
CIEM would have helped identify and revoke unused permissions, closing the gaps that attackers exploited.
Midnight Blizzard Campaign: How CIEM Could Have Made A Difference
In the Midnight Blizzard espionage campaign, the attackers exploited weaknesses in entitlement management, specifically targeting cloud environments where permissions were either overly broad or poorly monitored. This allowed them to move laterally within the systems, accessing sensitive data.
How CIEM could have helped prevent the attack:
CIEM tools continuously monitor permissions usage, flagging anomalies in real time.
By enforcing least privilege principles, CIEM could have limited the attackers' ability to gain unauthorised access to critical cloud resources.
Real-time visibility into permission changes would have helped security teams detect and stop the attackers before they moved deeper into the system.
Looking forward
While the data on misused and overprivileged identities highlights critical challenges there is hope. Vendors like Microsoft are addressing these risks head-on CIEM tools such as Microsoft Entra Permissions Management are proving effective. According to the 2024 State of Multi-cloud Security Report there has been notable progress since the 2023 State of Cloud Permissions Risks Report we referenced eclair.
TL;DR: Managing human and machine identities in multi-cloud environments is complex and risky. Recent breaches, like the Okta October 2023 incident and Midnight Blizzard espionage, expose vulnerabilities from overprivileged access. Cloud Infrastructure Entitlement Management (CIEM) helps mitigate these risks by automating identity and permission management, ensuring least privilege access, and providing real-time visibility.
Have blog ideas, want to engage on a topic, or explore collaboration? Let’s take it offline reach out on LinkedIn. I’d love to connect and continue the conversation!