Defender For Cloud - under the hood: Recommendations deep dive
Learn about the corner stone of Microsoft Defender For Cloud, security recommendations
If your cloud misconfigurations are multiplying faster than your email spam (and we all know how fast that is), it’s probably time to take a closer look 👀🔴 Defender for Cloud makes it easy to find, investigate and remediate recommendations using the dedicated recommendations tab.
‼️) This blog is part of a Defender For Cloud "Under the hood series" where we explore the various features, benefits and considerations that come with implementing Defender For Cloud (and other CNAPPs). You don't need any prior experience just a willingness to learn and develop. I don't quite know when the series will end but I hope you enjoy.What are recommendations?
Security recommendations form the core of any Cloud-Native Application Protection Platform (CNAPP), including Microsoft Defender for Cloud. These recommendations provide actionable security guidance to help reduce your attack surface. They are typically based on industry best practices and compliance frameworks such as CIS, NIST, and ISO. By remediating these recommendations, organisations can strengthen their security posture and align with regulatory requirements.
Recommendations are generated by assessing your cloud environment to identify misconfigurations, vulnerabilities, or security risks. They help improve your overall security posture by guiding you on what actions to take to reduce your overall attack surface.
How are recommendations generated?
Security recommendations can come from any of the integrated functions within the broader CNAPP framework, including CSPM, CIEM, and CWPP, and are not limited solely to cloud security posture management. As a unified platform, CNAPP leverages contextualised data, risk correlation, and workload runtime protection to provide comprehensive security insights and end-to-end visibility across cloud environments. When you deploy assets that deviate from best practices or violate a compliance standard assigned to your cloud environment, a recommendation will be generated.
An important note: To start receiving security recommendations in defender for cloud, you must select an industry standard or regulatory compliance framework. By default, the Microsoft Cloud Security Benchmark (MCSB) is applied to AWS, Azure, and GCP resources as soon as you enable Microsoft Defender for Cloud.
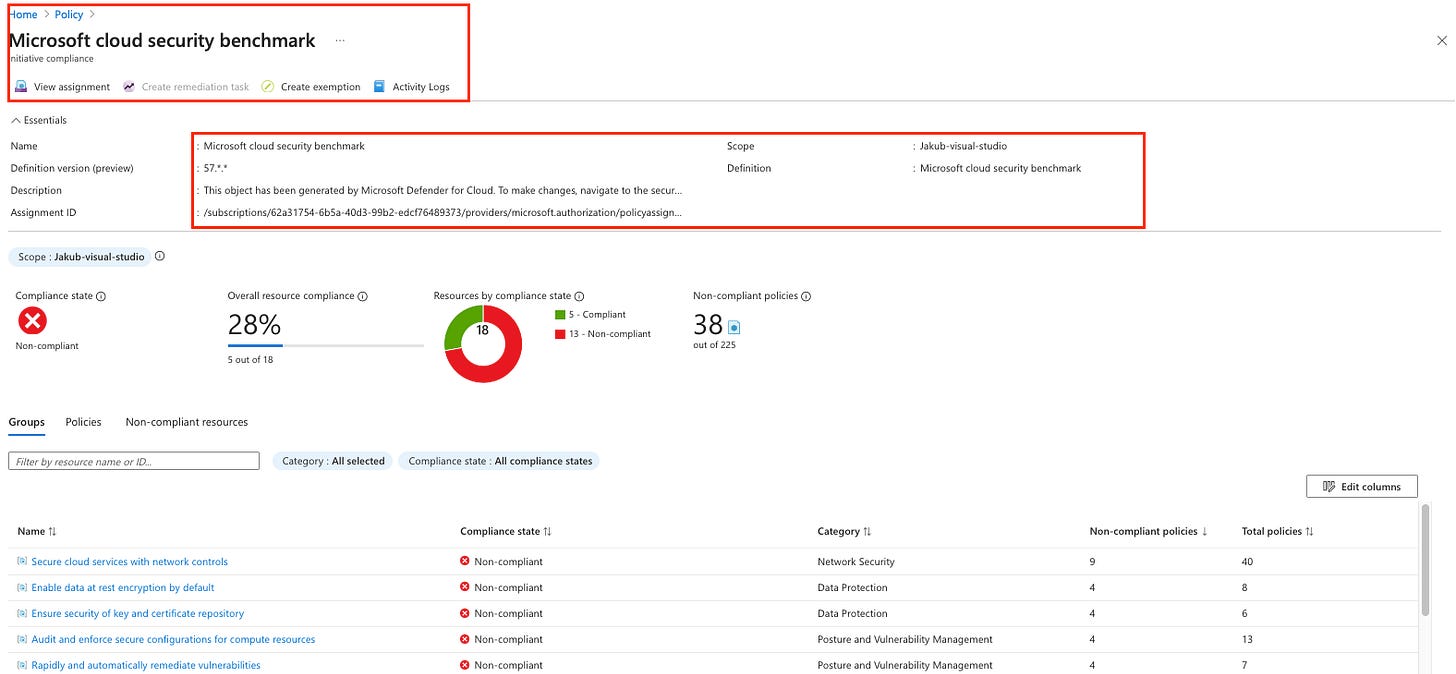
The security recommendations you see in the Defender for Cloud UI are generated using Azure Policy definitions and initiatives. However, for non-Azure resources (AWS and GCP), recommendations are based on Defender for Cloud’s built-in security standards and assessment mechanisms. These are integrated directly into Defender for Cloud, meaning they don’t rely on Azure Policy to evaluate security posture. Custom security standards are also supported, but this blog won’t cover them.You can find compliance and industry standards in Azure Policy within the Azure portal, under Policy Definitions.
If you're interested in how these policies are structured, click on an industry standard or compliance framework. Once inside, you’ll be able to view the policy definition.
The Azure Policy page also gives you an overview of how compliant your environment is with a particular industry standard or compliance framework.
In the Environment Settings, you can select your subscription (or a management group) to see which security standards you have enabled. This is also where you can enable additional standards, provided you’re eligible based on your Defender for Cloud plan:
MCSB is included in the foundational CSPM plan.
For additional standards, you’ll need the paid CSPM plan.
If you ever need to check which security recommendations are available for your selected standards, head to the Recommendations tab. Here, you’ll find detailed information on the different types of recommendations and the industry standards or compliance frameworks they align with.
How does a recommendation impact my security posture?
Each cloud provider has its own way of assessing the impact of security recommendations. In Microsoft Defender for Cloud, this impact whether a recommendation is completed or not is tracked using Secure Score.
Since Secure Score is a deep topic, I’ll cover it in a separate blog.The Recommendations Page
Now that we’ve covered the basics (see the references section for more reading), let’s dive into the Defender for Cloud console.
You’ll find recommendations in multiple places within Defender for Cloud but don’t worry, they all show the same information. Since you’ll spend a lot of time working from this dashboard, my best advice is to get familiar with it, as it’s a key part of managing your security posture.
Where to Find Recommendations
Overview Page – The Security Posture tab links to the Recommendations Page. It also gives a quick overview of:
The number of recommendations, categorised by risk level
Attack paths
Overdue recommendations, which serve as a governance feature
Recommendations Tab – This takes you directly to the Recommendations Dashboard.
Filtering and Exporting Recommendations
The filters allow you to refine the recommendations based on environment, helping you focus on specific security areas. You can also export filtered recommendations for external reporting.
In previous blogs, I mentioned that Defender for Cloud integrates with Azure Resource Graph (ARG). Unlike the pre-built filters, ARG lets you query security data at scale across multiple subscriptions or environments. This provides deeper insights than the standard UI, making it a powerful tool for advanced security analysis.
The Governance Report tab is based on workbooks and governance rules both of which will be covered in a separate blog due to their depth.What can you expect to see in a recommendation?
Microsoft Defender for Cloud continuously analyses and assesses the security state of your protected resources against defined security standards. This helps identify misconfigurations and security weaknesses. Based on its findings, Defender for Cloud provides recommendations to help strengthen your security posture.
Each recommendation is assigned a risk level, which reflects how exploitable and impactful the issue is within your environment. The risk assessment engine takes into account factors such as:
Internet exposure
Data sensitivity
Lateral movement potential
Attack path remediation
You can prioritise recommendations based on their risk levels. Some recommendations may also lead to attack paths, which can be investigated using the Attack Path Analysis (APA) feature covered in another blog in this series.
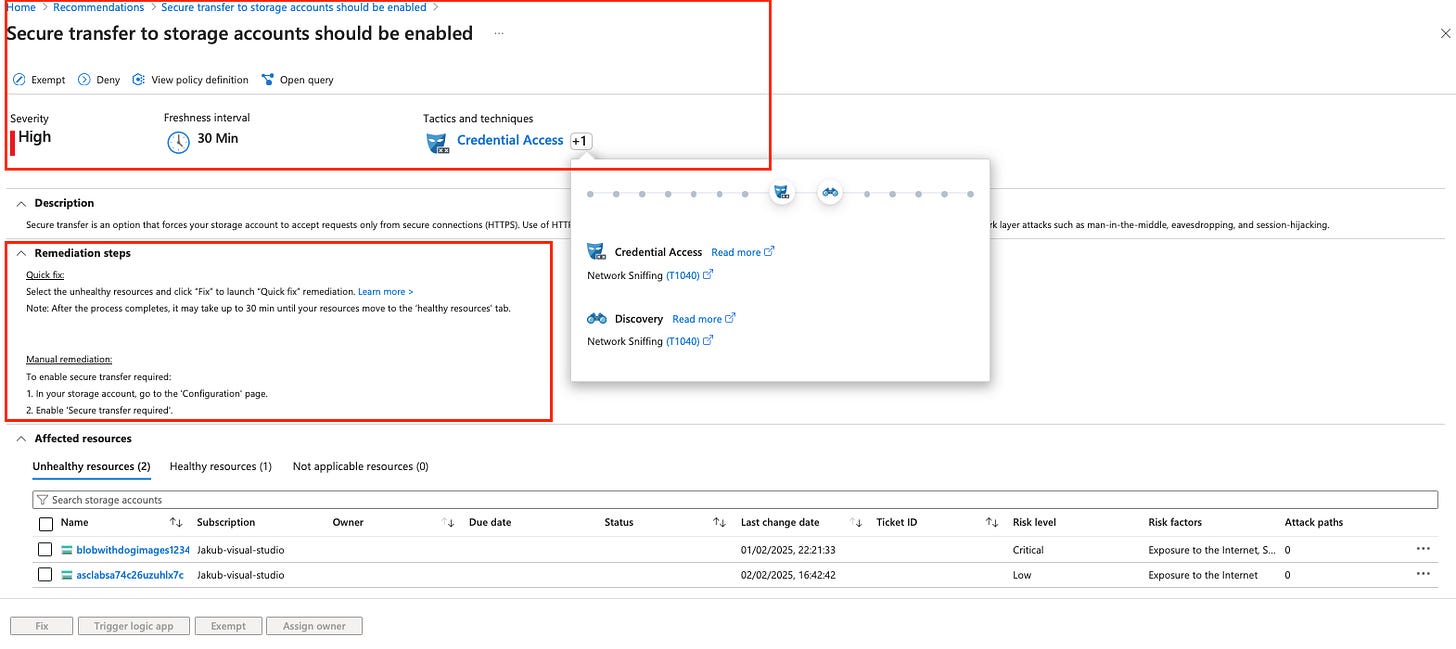
Breakdown of a Recommendation
Each recommendation provides key details, including:
Risk Level – Evaluates how exploitable the security issue is and its potential business impact, factoring in resource context (e.g. internet exposure, sensitive data, and lateral movement risks).
Risk Factors – Highlights environmental aspects that influence exploitability and impact (e.g. internet exposure or lateral movement potential).
Resource – The affected resource.
Status – The current state of the recommendation (e.g. unassigned, on time, overdue).
Description – A brief summary of the security issue.
Attack Paths – The number of potential attack paths linked to this issue.
Scope – The impacted subscription or resource.
Freshness – How often the recommendation is updated.
Last Change Date – The last time the recommendation was modified.
Severity – The criticality of the issue (High, Medium, Low).
Owner – The person responsible for resolving the recommendation (part of the governance feature).
Due Date – The deadline for remediation.
Tactics & Techniques – The relevant MITRE ATT&CK tactics and techniques linked to the issue. (More details on this can be found in my blog post on Attack Path Analysis.)
Recommendations contribute to your Secure Score—a single metric that aggregates security findings, giving you an at-a-glance view of your overall security status. A higher score means a lower overall risk level. Due to its depth, Secure Score is covered in detail in a separate blog post.What can you do with a recommendation?
Once a recommendation is generated in Microsoft Defender for Cloud, you have several actions available to manage, investigate, or remediate it.
Open query: View detailed information about the affected resources using an Azure Resource Graph (ARG) query. This option will allow you to get more data from the recommendation such as the impact of the recommendation on your secure score.
View policy definition: Check the Azure Policy entry linked to the recommendation. The Azure policy is the logic that created the recommendation and evaluates against it as discussed above.
View recommendation for all resources shows the same recommendation but for all affected resources. Clicking into this view provides several options. Before diving into those, let’s cover a few key aspects. Interval freshness refers to how frequently the recommendation is evaluated—either by Azure Policy for Azure resources or by Defender for Cloudfor AWS and GCP resources. Additionally, tactics and techniques are mapped to the MITRE ATT&CK® framework.
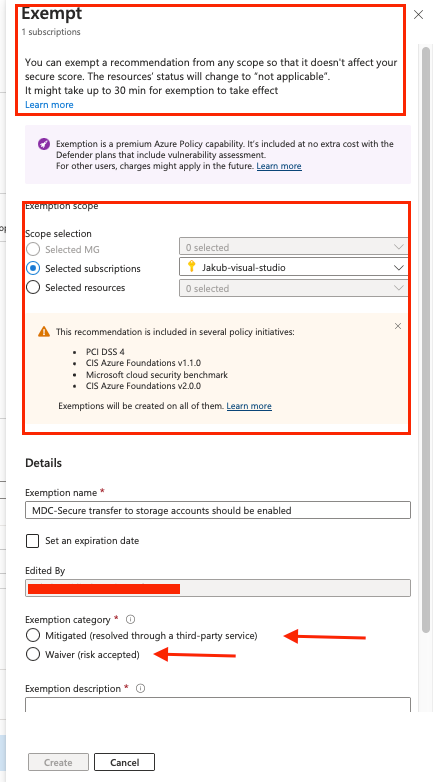
Exempt option: The Azure Policy exemptions feature is used to exempt a resource hierarchy or an individual resource from evaluation of initiatives or definitions by extension excluding the resource from future defender for cloud recommendations for that specific control.
Exemptions can be applied at different levels, giving you flexibility in managing recommendations:
Individual resource – Exempt a specific resource from evaluation.
Resource group – Apply the exemption to all resources within a group.
Subscription – Exclude all resources in a subscription.
Management group – Apply exemptions across multiple subscriptions.
Additionally, you can set an expiration date for temporary exemptions, which is useful for testing scenarios or short-term exclusions.
Exemption Categories:
When exempting a recommendation, you must select a category:
Resolved through a third party (Mitigated) – Choose this if you're using a third-party security solution that Defender for Cloud doesn’t recognize. (Note: Secure Score will not increase for this exemption.)
Risk Accepted (Waiver) – Use this when you acknowledge the risk but decide not to mitigate the recommendation.
Before applying exemptions, keep the following in mind:
Some Microsoft Cloud Security Benchmark recommendations cannot be exempted (a reference list is available).
If a recommendation appears in multiple policy initiatives, you must exempt it across all initiatives.
Custom recommendations cannot be exempted.
If a recommendation is disabled, all sub-recommendations under it are automatically exempted.
Under the hood: When you exempt a resource from a recommendation, it no longer affects your secure score. If you exempt specific resources, they’ll appear under the Not applicable tab on the recommendation details page. If you exempt an entire recommendation, it will be hidden by default on the Defender for Cloud recommendations page. This happens because the Recommendation status filter is set to exclude Not applicable recommendations by default. The same applies if you exempt all recommendations within a security control.
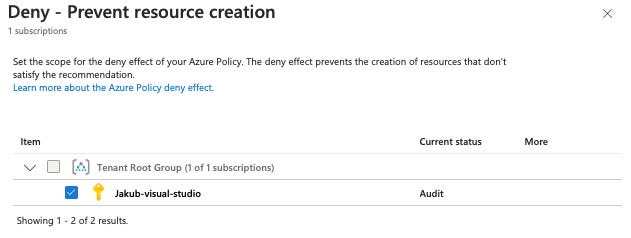
The Deny effect prevents non-compliant resource requests from being created in Azure. This is enforced via Azure Policy and is useful for establishing guardrails at the subscription level.
Example:
If a virtual machine (VM) is deployed without encryption, the request will be denied. This ensures that security standards are enforced before a misconfigured resource is created.
Limitations & Considerations
Deny is only available for Azure recommendations.
AWS and GCP do not support enforcement via Azure Policy.
Currently, Deny cannot be applied at the resource group or individual resource level—it is only supported at the subscription level.
Under the hood: Both enforce and Deny are applicable to Azure recommendations and are supported on a subset of recommendations. This is because AWS or GCP can't be enforced via Azure Policy. Take action on the recommendation available options:
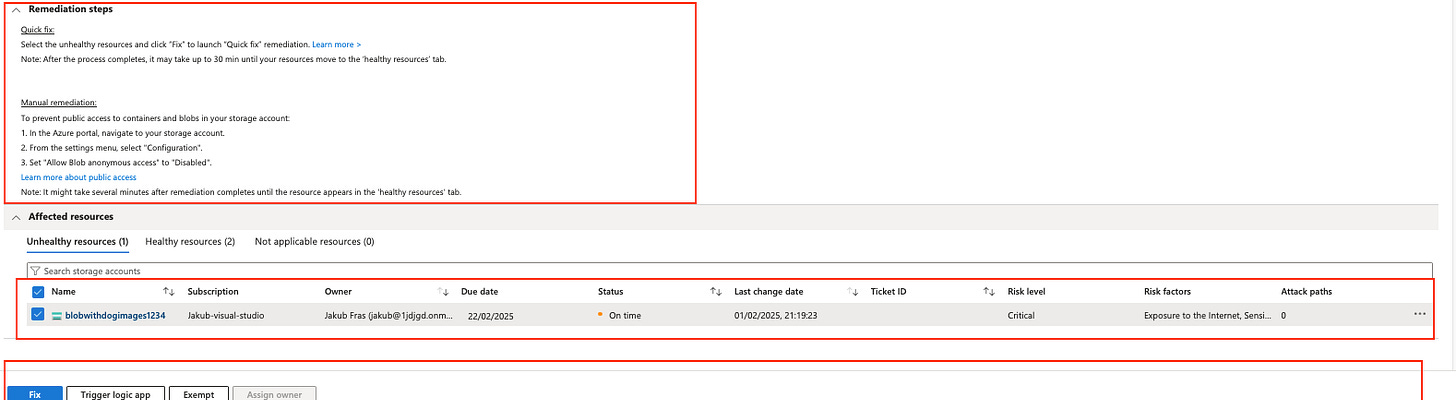
You’ll see the remediation options both from the individual recommendation page and View recommendation for all resources page.
The remediation process and available actions are covered in detail in another blog post within this series. 🚀Reference:
Learn About Security policies in Defender For Cloud
Learn about Risk prioritisation
Learn about KQL - A book by Rod Trent Must Learn KQL
Defender For Cloud GitHub Labs
Defender for Cloud Feature requests
Defender for Cloud in the field show
Defender For Cloud Ninja training
Have blog ideas, want to engage on a topic, or explore collaboration? Let’s take it offline reach out on LinkedIn. I’d love to connect and continue the conversation!