Defender For Cloud - under the hood: Defender For Servers P1
Learn Why Defender for Servers is Essential for Cloud Security and how your server workloads are protected
Securing server workloads in Azure, AWS, GCP, and on-premises requires more than just standalone endpoint protection. In this blog, I’ll cover what Defender for Servers is, how it works, and key product features, helping you understand the often miss understood or confused capability.
‼️) This blog is part of a Defender For Cloud "Under the hood series" where we explore the various features, benefits and considerations that come with implementing Defender For Cloud (and other CNAPPs). You don't need any prior experience just a willingness to learn and develop. I don't quite know when the series will end but I hope you enjoy.What is Defender For Servers?
The Defender for Servers plan in Microsoft Defender for Cloud is designed to protect server workloads. It goes beyond threat detection and response by offering additional features:
Protect multi-cloud and on-premises machines: Defender for Servers protects Windows and Linux machines in multi-cloud environments (Azure, AWS, GCP), and on-premises.
Under the hood… To access the complete feature set, Azure Arc is required for non-Azure machines.Centralised management and reporting: Defender for Cloud provides a single view of monitored resources, including machines protected by Defender for Servers.
Integration with DFE and XDR: Defender for Servers integrates natively with security capabilities provided by Defender for Endpoint and Microsoft Defender Vulnerability Management. As well as the Microsoft XDR stack meaning you’ll get the full data correlation capabilities and benefits.
Improve cloud security posture and reduce risk: Defender for Servers evaluates machines against compliance standards (e.g. CIS, NIST, MCSB) and provides security recommendations to improve overall protection.
Why do we need defender for servers?
I get asked this a lot: “Jakub, why can’t we just install Defender for Endpoint on this VM?” Let’s break it down.
First, it’s important to understand that server security in the cloud is different from traditional endpoint security. You need an additional security layer to protect not just the server itself, but also the cloud-native control plane around it things like networking, storage, and the operating system. On top of that, you need tools to assess misconfigurations and vulnerabilities across multi-cloud and hybrid environments.
While Defender for Servers and Microsoft Defender for Endpoint share some capabilities and are integrated, Defender for Endpoint alone is an Endpoint Detection and Response (EDR) solution. EDR focuses on monitoring endpoints in real time to detect and respond to potential threats. However, it does not provide the broader security visibility and controls needed for cloud and hybrid server workloads.
Defender for Servers builds on Defender for Endpoint, adding extra layers of security and deeper insights into server workloads across Azure, AWS, Google Cloud, and on-premises environments.
For more details, check out the Defender for Cloud in the Field episode, where the product team explains this in depth:
More on these features, defender for Servers offers two plans:
What Both Plans Include (Plan 1 & 2)
Multi-cloud & hybrid protection: Works with Azure, AWS, GCP and on-premises machines when connected to Defender for Cloud
In the Cloud Workload Protection dashboard, you can see any unprotected VMs across your onboarded clouds and on-premises environments. If needed, you can upgrade machines to Defender for Servers Plan 1 or 2 directly from the portal.
Microsoft Defender for Endpoint (MDE) automatic onboarding: When Defender for Servers is enabled, MDE integration is turned on by default. This automatically deploys the Defender for Endpoint agent, extending endpoint detection and response (EDR) capabilities to servers..
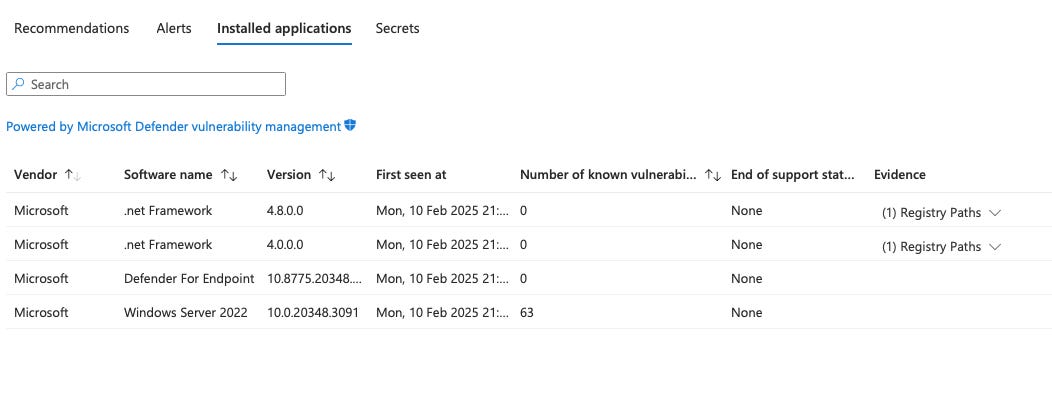
Under the hood: The Defender for Endpoint extension enables integration between Defender for Cloud and Defender for EndpointYou can verify the Defender for Endpoint agent is installed by checking the Installed Applications tab in the Resource Inventory blade like i’ve done below:
OS-level threat detection: Defender for Endpoint provides real-time threat detection at the operating system level.
Integrated alerts & incidents: Defender for Endpoint alerts are visible in Defender for Cloud and can be investigated further in the Defender portal.
I covered alert integration in a previous blog it's enabled by default for new tenants.
Software inventory discovery: Defender Vulnerability Management integrates with Defender for Cloud to track installed software.
Vulnerability scanning (agent-based): The Defender for Endpoint agent enables Defender for Cloud to scan machines for security vulnerabilities.
You can filter vulnerabilities across virtual machines in Defender for Cloud and get the same level of context as in the XDR portal.
Regulatory compliance assessment: Includes foundational security compliance standards from the MCSB, with additional compliance frameworks available when a Defender plan is enabled.
Additional Features in Plan 2
Agentless security features
Agentless vulnerability scanning: Defender for Cloud scans machines for vulnerabilities without requiring an agent, supplementing agent-based scanning.
Agentless malware scanning: Scans for malicious files without needing additional software installation. Read more on how malware scanning works.
Agentless secrets scanning: Detects exposed credentials stored in plain text on machines. Secret scanning uses Defender for Cloud CSPM to scan and capture disk snapshots for analysis with no impact on performance. Read more on how secret scanning works.
Under the hood these capabilities are provided by cloud security posture management (CSPM) and Defender For Endpoint EDR and vulnerability management capabilities
Upcoming blogs will dive deeper into the malware scanning architecture and other advanced features.
Enhanced threat detection:
Azure network-layer threat detection: Identifies security threats targeting the Azure network control plane, providing network-based alerts for Azure VMs. Aside from alerts you’ll also get networking specific hardening recommendations.
Example: Defender for Cloud correlates network activity to detect suspicious traffic patterns like in the alerts you see above. View the full reference of network layer alerts.
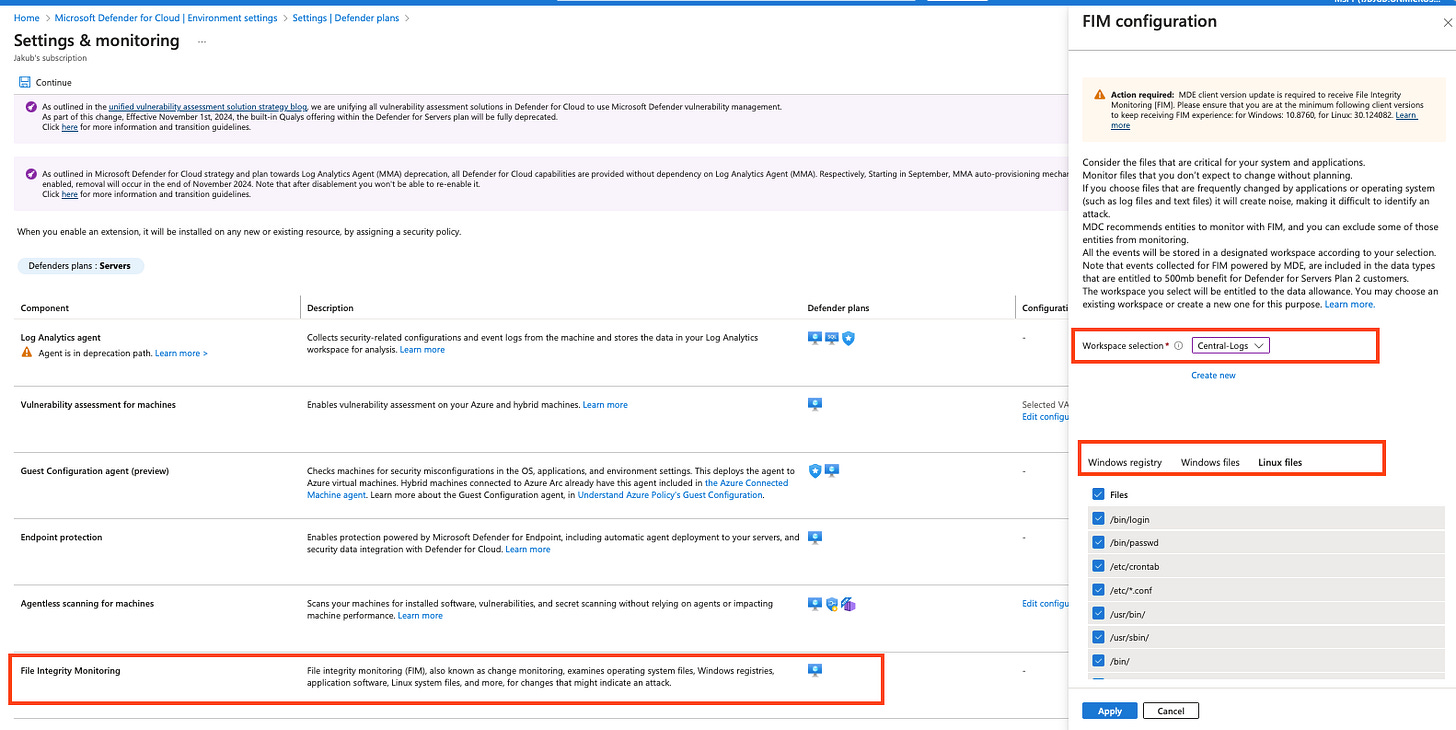
File integrity monitoring (FIM): Tracks changes to critical files and registries to detect unauthorised modifications and indicators of potential attacks or malware such as ransomware. File integrity monitoring provides information about file and resource changes, including the source of the change, account details, indication of who made the changes, and information about the initiating process. The data is stored within the log analytics workspace.
Under the hood: File integrity monitoring uses the Microsoft Defender for Endpoint agent to collect data from machines.Security configuration & compliance
OS security baseline assessments: Evaluates machine configurations against security baselines for Windows and Linux.
Defender for Cloud assesses and enforces security configurations using built-in Azure policy initiatives, including its default Microsoft Cloud Security Benchmark (MCSB) initiative. The Machine Configuration extension performs audit and configuration operations inside virtual machines (VMs) and MUST be installed.
Read more about baselines here
Read more about the Machine configuration extension here
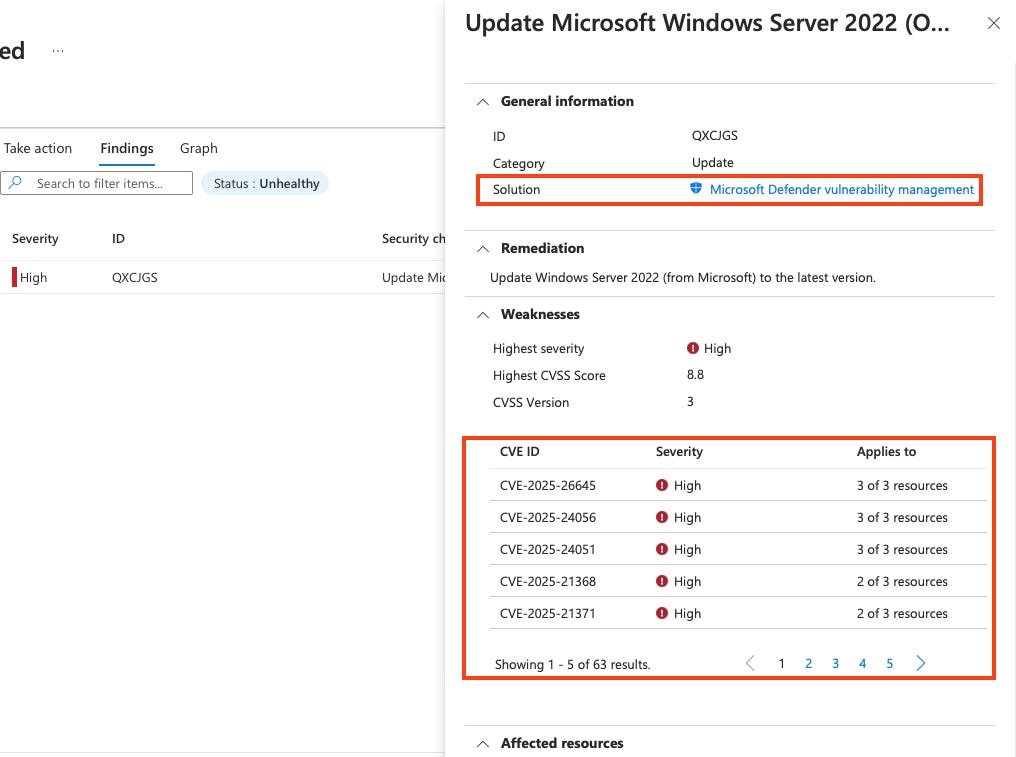
OS system updates tracking: Uses Azure Update Manager to assess whether critical updates and patches are installed. On-premises, AWS, and GCP machines must be onboarded with Azure Arc to use this feature.
Clicking “FIX“ will launch the out of the box remediation workflow to enable the extension on the machine and check for periodic updates, you can verify this in azure update manager.
Enabling periodic assessments for Arc enabled machines that Defender for Servers Plan 2 is not enabled on their related Subscription or Connector, is subject to Azure Update Manager pricing. Arc enabled machines that Defender for Servers Plan 2 is enabled on are included.Defender for Vulnerability Management premium features: Includes additional assessments like certificate security checks and OS baseline compliance.
To view details about OS baselines and certificates you'll need to use the XDR portal and create a baseline. Due to the feature complexity we'll cover it in another blog.Additional security tools
Just-in-time (JIT) VM access: Reduces exposure to attacks by restricting access to VMs, allowing connections only when needed (and approved).
Network map: Provides a visual overview of network security posture, showing recommendations to improve security. The interactive network map provides a graphical view with security overlays giving you recommendations and insights for hardening your network resources. Using the map you can see the network topology of your Azure workloads, connections between your virtual machines and subnets, and the capability to drill down from the map into specific resources and the recommendations for those resources.
Log analytics benefits
Free data ingestion (500 MB per day): Plan 2 includes 500 MB of free data ingestion for specific security-related logs in Log Analytics workspaces*. More about this benefit in the deployment blog.
We are only scratching the surface really to what these features can do and how well they workload together to provide layered security. feel free to visit the official documentation to read more about them.Deployment scope and method
In the next blog we’ll cover the deployment options in detail both for cloud and on premises servers.
Reference:
Defender For Cloud GitHub Labs
Defender for Cloud Feature requests
Defender for Cloud in the field show
Defender For Cloud Ninja training
Have blog ideas, want to engage on a topic, or explore collaboration? Let’s take it offline reach out on LinkedIn. I’d love to connect and continue the conversation!