Defender For Cloud - under the hood: Defender For Servers vulnerability management
Defender for servers vulnerability management how it works?
If you're like me, navigating the complexities of cloud and hybrid environments, you know that our attack surface has grown massively. It's a challenge keeping track of every potential nook and cranny attack paths can crop up from the simplest misconfiguration and what seems to be a small vulnerability could serve as a pivot point for an attacker. That's why I believe proactive vulnerability management isn't just a good idea anymore it's absolutely essential to our cybersecurity strategy.
I wanted to share my in-depth look at Defender for Cloud's vulnerability management features focusing on servers and not specifically endpoints the two differ in provided functionality. We'll unpack what it can do, clarify the agentless vs. agent-based scanning approaches, look at the latest plan requirements, cover the essential prep work for getting it up and running, and talk about what's included and what's not.
Getting Defender for Cloud's vulnerability management up and running smoothly means ticking off a few prerequisite boxes. Trust me, planning this out saves a lot of trouble.
Core plan and needs
Your scanning choice dictates the plan:
Agentless Scanning: You'll need Defender for Servers Plan 2. When you turn on Defender for Servers Plan 2 or the Defender Cloud Security Posture Management (CSPM) plan, agentless machine scanning is enabled by default as other features from the CSPM plan like software inventory discovery rely on it therefore it will be turned on.
Agent-Based Scanning: This relies on Microsoft Defender for Endpoint (MDE) integration, so you need Defender for Servers Plan 1 or Plan 2 active. MDE integration must also be enabled.
Foot notes: Defender Vulnerability Management premium capabilities are available to server devices with Microsoft Defender for Servers Plan 2. Learn more about premium capabilities. Something important to know based on the documentation * which could be clearer Vulnerability scanning (agentless) is only supported by defender for servers plan 2 you can verify this here which obviously means no agentless for plan 1.
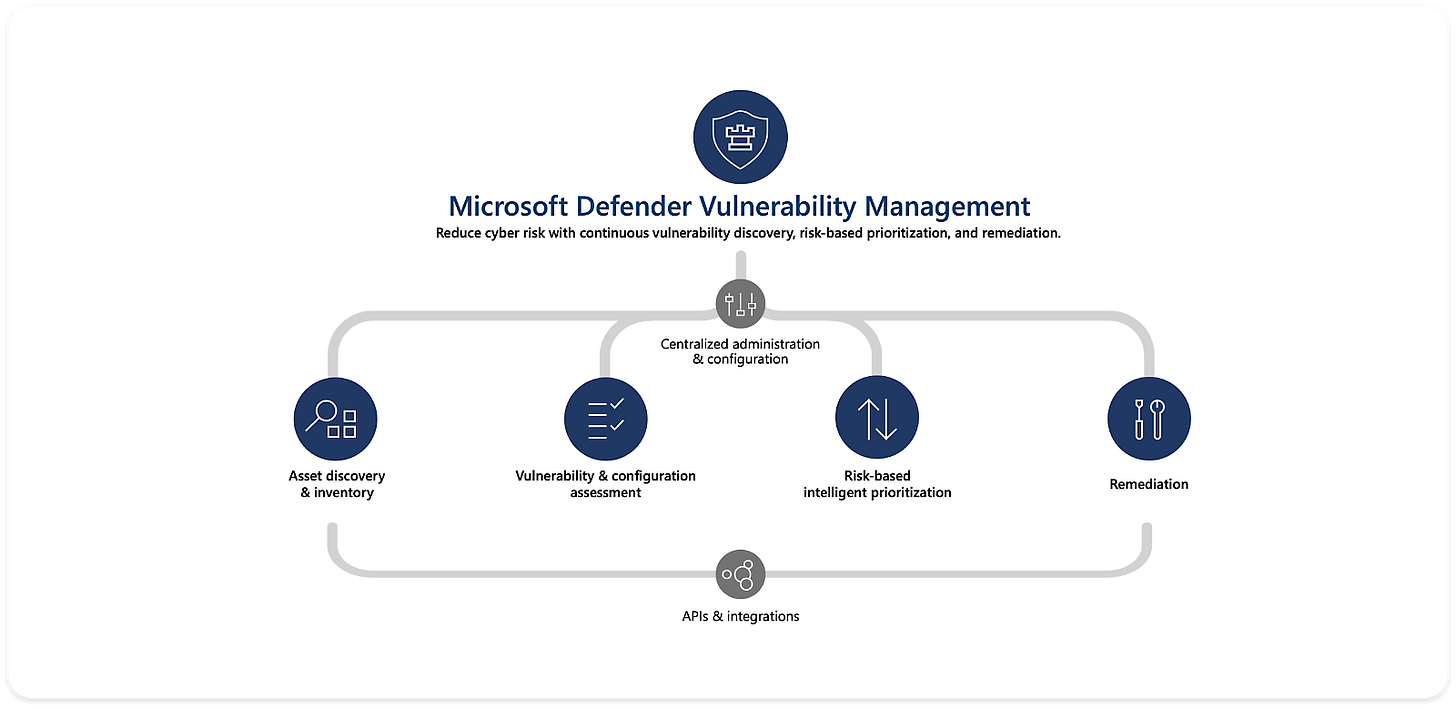
Defender for Servers Vulnerability Management how it works
At a glance:
Continuous Discovery and Monitoring:
Defender for Cloud, leveraging Microsoft Defender Vulnerability Management, automatically discovers and monitors the software installed on your servers (Azure VMs, AWS/GCP VMs, and on-premises machines connected via Azure Arc).
This process is continuous, providing near real-time visibility into your server's software inventory.
Vulnerability Assessment:
Defender for Servers uses either agent-based (leveraging the Microsoft Defender for Endpoint agent) or agentless scanning (available in Defender for Servers Plan 2) to identify vulnerabilities.
These scanners analyze the installed software and compare it against a continuously updated database of known vulnerabilities (CVEs).
Risk-Based Prioritization:
Defender Vulnerability Management doesn't just list vulnerabilities; it intelligently prioritizes them based on:
Microsoft Threat Intelligence: Insights into which vulnerabilities are actively being exploited in the wild.
Breach Likelihood Predictions: Analysis of the potential for a vulnerability to be exploited.
Business Context: Identification of critical assets, high-value users, and sensitive data.
Device Assessments: The specific configuration and security posture of the server.
This prioritization helps you focus on the most critical vulnerabilities that pose the highest risk to your environment.
Actionable Security Recommendations:
Defender for Cloud presents prioritised security recommendations within the Azure portal.
These recommendations provide details about the identified vulnerabilities, the affected servers, and clear remediation steps to mitigate the risk.
Integration with Microsoft Defender for Endpoint:
If you're using Defender for Servers Plan 1 or 2, it integrates with Microsoft Defender for Endpoint. This provides a unified view of endpoint and server vulnerabilities and threats.
Premium Vulnerability Management Features (Defender for Servers Plan 2):
Plan 2 unlocks additional premium capabilities, including:
Security Baselines Assessment: Compare your server configurations against industry benchmarks like CIS and STIG.
Software Usage Insights: Understand how software is being used to identify potential risks.
Block Vulnerable Applications: Prevent users from running known vulnerable applications.
Browser Extensions Assessment: Identify risky browser extensions installed on servers.
Digital Certificate Assessment: Manage and identify vulnerabilities related to digital certificates.
Network Share Analysis: Assess the security of internal network shares.
Hardware and Firmware Assessment: Identify vulnerabilities in server hardware and firmware.
Authenticated Scan for Windows: Improve the accuracy of vulnerability assessments on Windows servers by providing credentials for remote access.
In summary, Defender for Servers Vulnerability Management automates the process of identifying, prioritising, and providing remediation guidance for security vulnerabilities on your servers, helping you to proactively reduce your attack surface and improve your overall security posture.
Which recommendations will I see in Defender for cloud if Vulnerability Management is missing on my servers?
Multiple including Machines should be configured securely and Install endpoint protection solution on virtual machines the full list can be found here.
I have both agentless and agent based which one is prioritised
Machines using agent-based scanning OR agentless scanning show the results from that enabled source only. Machines with both agent-based and agentless scanning show the agent-based results only, for better freshness.
Getting Your Machines Onboard & Connected
Azure Native VMs: These are discovered automatically once their Azure subscription is under Defender for Cloud's wing.
On-Premises and Multicloud (AWS, GCP): For these, Azure Arc-enabled servers is your best friend. Azure Arc extends the Azure management plane (and Defender for Cloud's reach) to these non-Azure resources, making them manageable like they're in Azure.
Bring Your Own License (BYOL) for Vulnerability Scanners:
Integrating third-party scanners like Qualys and Rapid7 via BYOL is deprecated. As of early this year (in this context), you couldn't add new solutions or machines, and it's set for complete removal by May 1st. If you're still on BYOL, it's time to migrate to Microsoft's integrated Defender Vulnerability Management. The deprecation of both BYOL and the Authenticated Scan for Windows (Servers) really signals Microsoft's push towards its native, integrated solutions.
Inside the Azure Portal:
You’ll get your recommendations prioritised, if you want to know how this works i’ve covered recommendations and the engine that’s behind it in another blog within the series.
From the resource inventory you’ll also be able to tell if the server is using agentless or agent based typically from installed applications or under extensions of the server.
Vulnerabilities will influence your overall security posture, secure score and attack paths and will even influence exposure management that’s the power of a CNAPP a unified solution which is covered in detail in other blogs one of my favourite features is cloud explorer which you can also use ti proactively find attack paths in your environment.
Inside the XDR Portal:
As you likely know by now defender for cloud data is integrated with the XDR portal, the experience is slightly different and is designed for different personas but let’s break it down at a high level.
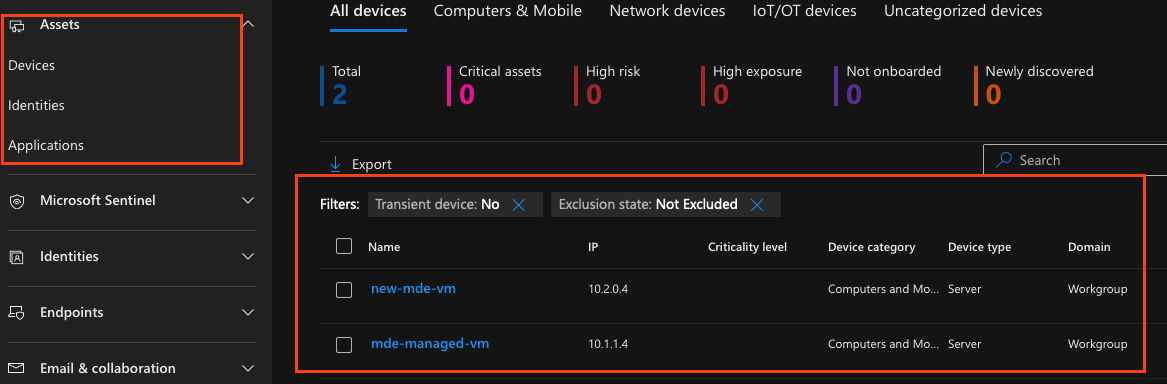
Today if you navigate to assets > select an asset you’ll be able to see the same vulnerabilities as within the defender for cloud portal.
Looking for more?
Have blog ideas, want to engage on a topic, or explore collaboration? Let’s take it offline reach out on LinkedIn. I’d love to connect and continue the conversation!