Defender For Cloud - under the hood: Cloud Security Explorer Deep Dive
Learn to proactively hunt for misconfigurations and vulnerabilities.
The blog builds on another post in the Defender for Cloud: Under the Hood series titled “Attack Path Analysis (APA) Deep Dive.” If you haven’t read it yet, I recommend starting there for some useful context.
‼️) This blog is part of a Defender For Cloud "Under the hood series" where we explore the various features, benefits and considerations that come with implementing Defender For Cloud (and other CNAPPs). You don't need any prior experience just a willingness to learn and develop. I don't quite know when the series will end but I hope you enjoy.What is Cloud Security Explorer?
Cloud Security Explorer builds on the Attack Path Analysis feature, helping you identify, investigate, and prioritise security risks to reduce your attack surface. It allows you to proactively hunt for potential entry points ( think vulnerabilities and misconfigurations) an attacker could use to move laterally and access sensitive resources within your multi cloud and hybrid environment. By taking a pro active approach your not just waiting for attack paths to appear using the attack path analysis (APA) feature instead your security team can use the query builder to search for and locate risks, considering your organisation's specific contextual and conventional information.
How does it work under the hood?
If you’ve been following the series, you should now have a solid understanding of the unified Cloud-Native Application Protection Platform (CNAPP) and its benefits. These include contextualised, risk-based prioritisation, end-to-end visibility, and data correlation across multiple solutions, including threat intelligence.
Cloud Security Explorer leverages all these CNAPP benefits and components ( CSPM, DSPM, CIEM) to correlate and visualise data into queries. In previous blogs, I also mentioned Cloud Security Graph a Microsoft proprietary algorithm designed to identify exploitable entry points and map out the steps an attacker could take to reach your critical assets. According to Microsoft each customer has unique cloud security graph that can be used to query for exploitable entry points based on their environment. Check out the below episode of defender for cloud in the field to find out more.
Query builder:
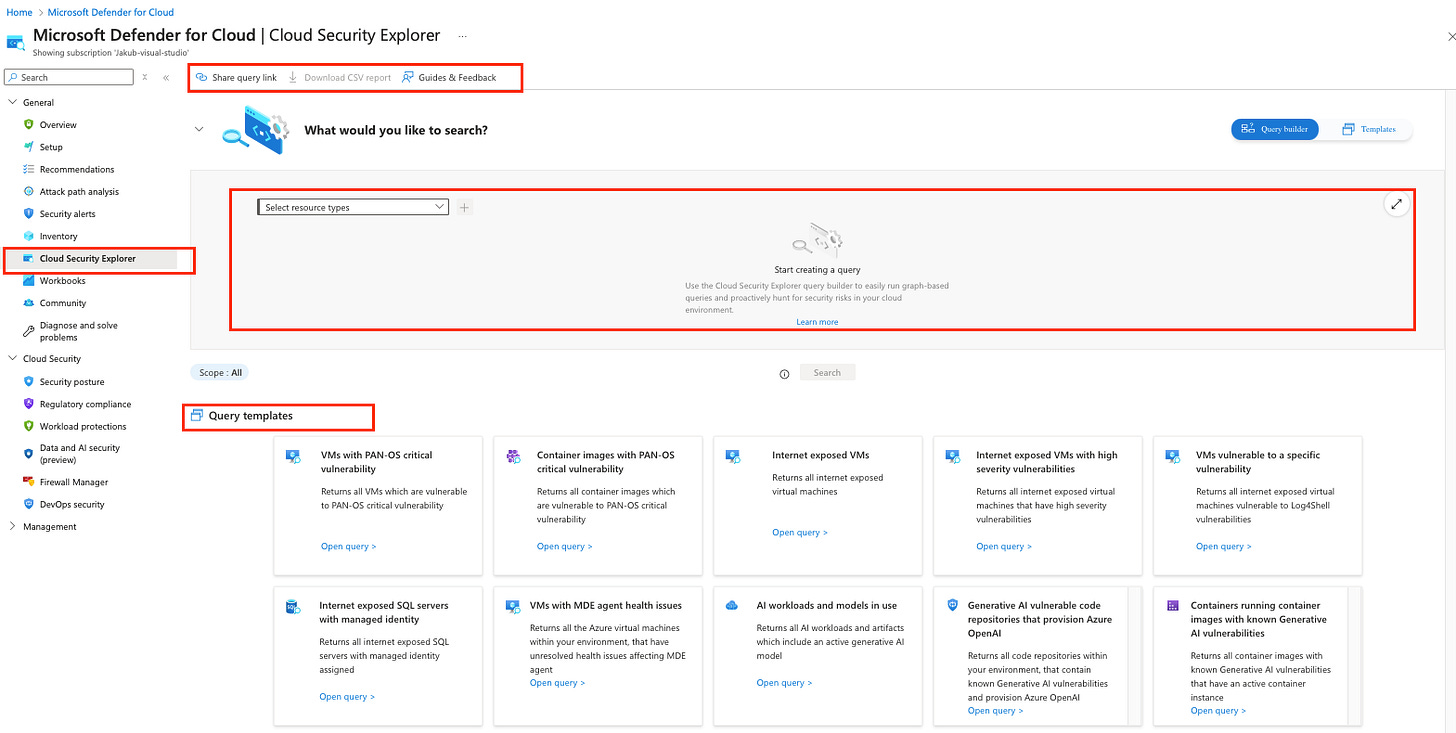
Once in the Defender for Cloud Portal and navigate to the cloud security explorer tab you’ll be able to proactively create your own queries or use the provided templates. The functionality helps in searching for security risks in your cloud environments with features like:
Multi-cloud and multi-resource queries – You can easily filter and group resources across different cloud environments to build your queries all at once.
Custom Search – Simply use the dropdown menus to apply filters and set up your query.
Query templates – There are pre-made query templates available to make things quicker and easier.
Share query link – Once you've built your query, you can copy and share the link with others.
Building your first query:
I really like this feature it's simple to use, with little complexity involved. As you can see below, I'm starting to build my custom query to proactively hunt for misconfigured and risky assets. I've selected VMs across Azure, AWS, and GCP.
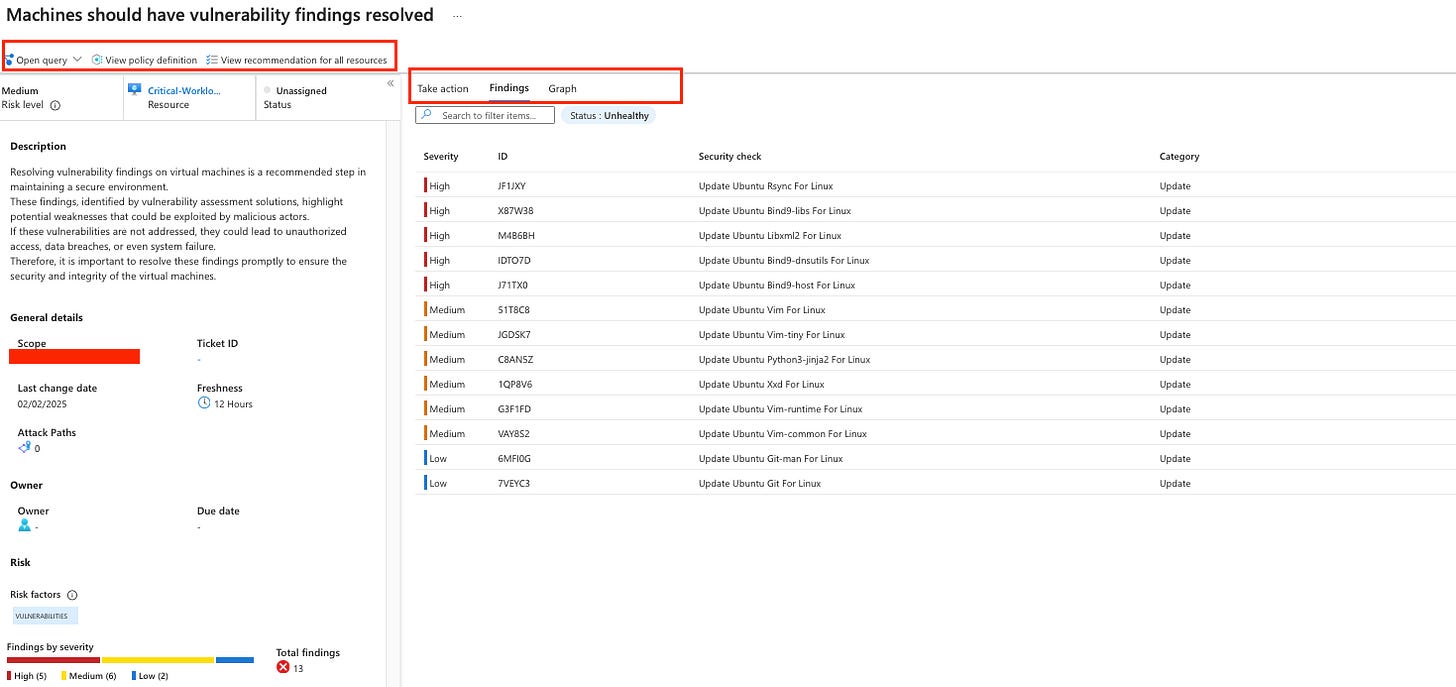
I then added a condition to display all the VMs in my environment with a critical vulnerability. It's worth noting that you can add multiple conditions at once to really fine tune the data you need. From my experience, I found the filter to be really effective.
Clicking “View details” will take me directly to the recommendation for the affected resource, where I can take action. I’ve covered recommendations in detail in another blog, so be sure to check it out as it’s the same experience.
Pre created templates:
As mentioned earlier, query templates are available right out of the box, allowing you to get started quickly without the need to build queries from scratch. These ready-made templates streamline your search for security risks, making it easier to find the information you need with minimal effort. Simply select a template, customise it if needed, and run your query—no complex setup required.
Can I query Cloud Security Explorer using an API or ARG?
Yes! 😀 Cloud Security Explorer and Attack Path Analysis (APA) are fully integrated with Azure Resource Graph (ARG), which can be queried using KQL, as shown in the example below, where I successfully retrieved my attack paths.
Reference for KQL tables can be found here and API documentation can be found here.
My KQL query for reference:
securityresources
| where type == "microsoft.security/attackpaths"
| where subscriptionId == "XXXXXXXX"
| extend AttackPathDisplayName = tostring(properties["displayName"])
| project AttackPathDisplayName, type, properties["description"], properties["manualRemediationSteps"], properties["potentialImpact"]Reference:
Learn about Risk prioritisation
Learn about KQL - A book by Rod Trent Must Learn KQL
Defender For Cloud GitHub Labs
Defender for Cloud Feature requests
Defender for Cloud in the field show
Defender For Cloud Ninja training
Have blog ideas, want to engage on a topic, or explore collaboration? Let’s take it offline reach out on LinkedIn. I’d love to connect and continue the conversation!